Supply Chain Cybersecurity Complaint Filed with FERC
Click Here for PDF Copy of Complaint
Click HERE for Federal Register Notice
Introduction
I am a private citizen who conducts public interest research on the security of the electric grid because I recognize the absolutely vital role of this infrastructure in powering every one of the nation’s 16 critical infrastructures and in undergirding not just the well-being but the very survival of our modern society.
I am filing this complaint under 16 U.S. Code § 824o(d)(5)[1] and 16 U.S. Code § 824o(e)(3)[2] because:
- The mandatory Critical Infrastructure Protection (CIP) standard CIP-013-1 (Cyber Security Supply Chain Risk Management) does not comport with Presidential Executive Order 13920: Securing the United States Bulk-Power System[3], and
- The Federal Energy Regulatory Commission (FERC) has not ensured that mandatory CIP standards “fully address leading federal guidance for critical infrastructure cybersecurity—specifically, the National Institute of Standards and Technology (NIST) Cybersecurity Framework.”
Request for Investigation
I request that the Commission issue a public notice of this Complaint pursuant to 18 CFR § 385.206(d), investigate this Complaint and issue an appropriate order to the Electric Reliability Organization (“ERO”) to correct deficiencies.
Background
On July 21, 2016 FERC issued Order No. 829, Revised Critical Infrastructure Protection Reliability Standards.[4] In this order, FERC:
“directs the North American Electric Reliability Corporation (NERC) to develop a new or modified Reliability Standard that addresses supply chain risk management for industrial control system hardware, software, and computing and networking services associated with bulk electric system operations.”
CIP-013-1 was developed by NERC and approved by FERC on October 26, 2018[5] although the implementation date has been delayed.[6] As of this filing, the standard has yet to be implemented – almost 4 years after FERC directed the standard.
Notwithstanding the bureaucratic delays and onerous process to develop a standard, NERC has demonstrated a lack of urgency in protecting the bulk power system. This was clearly evidenced on February 14, 2019 in the Senate Committee on Energy and Natural Resources hearing entitled: “Hearing to Consider the Status and Outlook for Cybersecurity Efforts in the Energy Industry.”[7]
Senator Angus King questioned NERC CEO James B. Robb on the supply chain risk management issue:
Sen. King: “Okay let me ask another question. Do any of our utilities have Kaspersky, Huawei, or ZTE equipment in their system?”
Mr. Robb: “We issued a NERC alert…”
Sen. King: “I didn’t ask you if you issued an alert. I asking you do any of our utilities have ZTE, Huawei, or Kaspersky equipment or software in their system?”
Mr. Robb: “Not to my knowledge.”
Sen. King: “Not to your knowledge. Have you surveyed any of the utilities to determine that?”
Mr. Robb: “Uhhh, I don’t believe we have.”
Sen. King: “I think that would be a good idea, don’t you?”
Mr. Robb: “I’ll take that on.”
In other words, two and a half years after FERC ordered the Cyber Security Supply Chain Risk Management standard, NERC hadn’t even checked to see if there is Russian or Chinese equipment or software installed on the electric grid.
Complaint 1. The mandatory standard CIP-013-1 (Cyber Security – Supply Chain Risk Management) does not comport with Presidential Executive Order 13920.
Against the protest of numerous commenters in the docket, CIP-013-1 fails to cover all systems in the bulk power system. Section 4.2.3.5 of the standard excludes:
“Responsible Entities that identify that they have no BES Cyber Systems categorized as high impact or medium impact according to the identification and categorization process required by CIP002-5, or any subsequent version of that Reliability Standard.”
In other words, the standard only covers high and medium impact systems and excludes supposed “low impact systems.” Unfortunately, the discretion is left to the individual companies in the industry to decide what is “low impact.”
On May 4, 2020, the President of the United States declared a national emergency and issued Executive Order 13920: “Securing the United States Bulk-Power System.” This action by the President is a vote of no-confidence in the lackadaisical and inadequate actions of FERC and NERC. The Commission and the ERO have not done enough to protect the bulk power system from cyber threats. This indictment of the lack of action on the part of FERC and the ERO must be remedied.
The Executive order requires that the Secretary of Energy:
- identify bulk-power system electric equipment designed, developed, manufactured, or supplied, by persons owned by, controlled by, or subject to the jurisdiction or direction of a foreign adversary that poses an undue risk of sabotage to or subversion of the design, integrity, manufacturing, production, distribution, installation, operation, or maintenance of the bulk-power system in the United States, poses an undue risk of catastrophic effects on the security or resiliency of United States critical infrastructure or the economy of the United States, or otherwise poses an unacceptable risk to the national security of the United States or the security and safety of United States persons; and
- develop recommendations on ways to identify, isolate, monitor, or replace such items as soon as practicable, taking into consideration overall risk to the bulk-power system.
This order invalidates the present scheme in CIP-013-1 in which each individual company has the discretion to decide the systems to which it wishes the standard to apply. The president of the United States has ordered the entire bulk power system protected.
Complaint 2. The Federal Energy Regulatory Commission (FERC) has not ensured that mandatory CIP standards fully address leading federal guidance for critical infrastructure cybersecurity—specifically, the National Institute of Standards and Technology (NIST) Cybersecurity Framework.
On May 21, 2008 Representative James R. Langevin, chairman of the House Subcommittee on Emerging Threats, Cybersecurity, and Science and Technology, in his opening statement to a hearing on cybersecurity[8] noted:
As time passes, I grow particularly concerned by NERC, the self-regulating organization responsible for ensuring the reliability of the bulk power system. Not only do they propose cybersecurity standards that, according to the GAO and NIST, are inadequate for protecting critical national infrastructure, but throughout the committee’s investigation they continued to provide misleading statements about their oversight of industry efforts to mitigate the Aurora vulnerability.
If NERC doesn’t start getting serious about national security, it may be time to find a new electric reliability organization. NERC can begin demonstrating its commitment by incorporating more of the NIST security controls in the next iteration of its reliability standards.
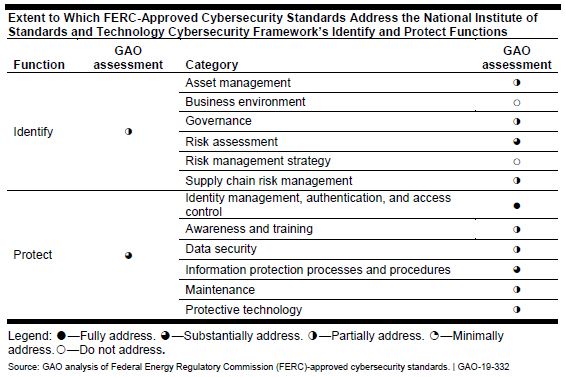
Emphasis added. That hearing was in 2008. Eleven years later, FERC and NERC had still failed to ensure that the mandatory CIP standards addressed the NIST cybersecurity framework. In September of 2019, the Government Accountability Office (GAO) issued a report[9] finding:
The Federal Energy Regulatory Commission (FERC)—the regulator for the interstate transmission of electricity—has approved mandatory grid cybersecurity standards. However, it has not ensured that those standards fully address leading federal guidance for critical infrastructure cybersecurity—specifically, the National Institute of Standards and Technology (NIST) Cybersecurity Framework.
Emphasis added. GAO include this table with their assessment of how well the current CIP standards address the NIST framework:
The President of the United States and Congress are not alone in their criticism of the lack of action by FERC and NERC to protect the bulk power system.
On September 6, 2019, Cybersecurity expert George Cotter submitted an assessment in FERC Docket AD19-18-000 and NP19-4-000 entitled “Security in the North American Grid, The Existential Threat. A White Paper.”[10] Mr. Cotter pointed out that:
“only 1374 of a total of 16,412 BES Transmission Substations qualified for CIP Standards based on Kv power minimums (over 90% excluded) and of the qualifiers, only 550 (40%) were estimated by their utilities to be critical to BES Reliability.”
In other words, the vast majority of facilities in the bulk power system are excluded from the CIP standards by their very design.
On May 4, 2020, Cybersecurity expert Joe Weiss pointed out in his blog[11] that:
“China and Russia have directly attacked the control system vendor supply chains since at least 2010. Many of the systems exploited and affected by adversaries are still used in the U.S. bulk and distribution power systems. Moreover, vendors supplying bulk (and distribution) electric equipment for the U.S. electric system also supplied similar (often the same) bulk and distribution electric equipment to other countries, including China, Iran, Russia, and Pakistan. (I include distribution systems, as it often uses the same equipment as transmission systems, and transmission directly “talks” to distribution – more discussions on distribution follows). Even bulk power equipment manufactured in the U.S. often use servers, processors, software, etc. that come from China which makes assuring supply chain integrity so difficult.”
And the supply chain threat is not hypothetical – it has actually happened. In his most recent article,[12] Mr. Weiss points out:
“So why the EO now? Government and public utility procurement rules often push organizations into buying equipment due to price and without regard to origin or risk. In this case, it resulted in a utility having to procure a very large bulk transmission transformer from China. When the Chinese transformer was delivered to a US utility, the site acceptance testing identified electronics that should NOT have been part of the transformer – hardware backdoors. That transformer now resides at a government installation.”
Our electric grid supply chain has already been targeted by state actors, as reported by Mr. Weiss and also by the Wall Street Journal. In a January 10, 2019 article,[13] the WSJ reported:
“A reconstruction of the hack reveals a glaring vulnerability at the heart of the country’s electric system. Rather than strike the utilities head on, the hackers went after the system’s unprotected underbelly—hundreds of contractors and subcontractors like All-Ways who had no reason to be on high alert against foreign agents. From these tiny footholds, the hackers worked their way up the supply chain. Some experts believe two dozen or more utilities ultimately were breached.”
On May 4, 2020, the President of the United States declared a national emergency and issued Executive Order 13920: “Securing the United States Bulk-Power System.” This is a true emergency and the Commission should act on this complaint with a sense of urgency.
Conclusion and Recommendations
The mandatory Critical Infrastructure Protection (CIP) standard CIP-013-1 (Cyber Security – Supply Chain Risk Management) does not comport with Presidential Executive Order 13920: Securing the United States Bulk-Power System.
As noted by Congress in 2008 and the GAO in 2019, the Federal Energy Regulatory Commission (FERC) has not ensured that mandatory CIP standards “fully address leading federal guidance for critical infrastructure cybersecurity—specifically, the National Institute of Standards and Technology (NIST) Cybersecurity Framework.”
- The Commission should direct NERC to Modify CIP-013-1 (Cyber Security – Supply Chain Risk Management) to cover every piece of equipment in the bulk power system with no exceptions including purported “low impact” BES cyber systems. Utilities should not have the discretion to decide what parts of the bulk power system they wish to protect.
- The Commission should direct NERC to revamp all CIP standards to “fully address leading federal guidance for critical infrastructure cybersecurity—specifically, the National Institute of Standards and Technology (NIST) Cybersecurity Framework.”
Respectfully submitted,
Michael Mabee
Attachment: 18 CFR § 385.206 Compliance Information
Click Here for PDF Copy With Exhibits
Footnotes:
[1] “The Commission, upon its own motion or upon complaint, may order the Electric Reliability Organization to submit to the Commission a proposed reliability standard or a modification to a reliability standard that addresses a specific matter if the Commission considers such a new or modified reliability standard appropriate to carry out this section.” [Emphasis added.]
[2] “On its own motion or upon complaint, the Commission may order compliance with a reliability standard and may impose a penalty against a user or owner or operator of the bulk-power system if the Commission finds, after notice and opportunity for a hearing, that the user or owner or operator of the bulk-power system has engaged or is about to engage in any acts or practices that constitute or will constitute a violation of a reliability standard.” [Emphasis added.]
[3] Attached hereto as Exhibit A.
[4] Available at: https://www.ferc.gov/whats-new/comm-meet/2016/072116/E-8.pdf (Accessed May 10, 2020).
[5] See: https://www.govinfo.gov/content/pkg/FR-2018-10-26/pdf/2018-23201.pdf (Accessed May 10, 2020).
[6] See 171 FERC ¶ 61,052, issued April 17, 2020.
[7] Available at: https://www.energy.senate.gov/public/index.cfm/hearings-and-business-meetings?ID=FE0534E7-2FC7-4DB0-BEA6-2634D3821ADD# (accessed October 19, 2019).
[8] “Implications of Cyber Vulnerabilities on the Resilience and Security of the Electric Grid.” Before the Committee on Homeland Security, Subcommittee on Emerging Threats, Cybersecurity, and Science and Technology. (110th Congress) May 21, 2008. https://www.gpo.gov/fdsys/pkg/CHRG-110hhrg43177/pdf/CHRG-110hhrg43177.pdf (accessed October 24, 2019). Hearing video available at: https://www.c-span.org/video/?205553-1/security-electric-grid (accessed October 24, 2019).
[9] U.S. Government Accountability Office. “Critical Infrastructure Protection: Actions Needed to Address Significant Cybersecurity Risks Facing the Electric Grid.” GAO-19-332: Published: Aug 26, 2019. Publicly Released: Sep 25, 2019. Copy attached hereto as Exhibit B. Also available at: https://www.gao.gov/products/GAO-19-332 (accessed October 22, 2019).
[10] Attached hereto as Exhibit C
[11] Attached hereto as Exhibit D
[12] Attached hereto as Exhibit E.
[13] Smith, Rebecca. The Wall Street Journal. “America’s Electric Grid Has a Vulnerable Back Door—and Russia Walked Through It.” January 10, 2019. https://www.wsj.com/articles/americas-electric-grid-has-a-vulnerable-back-doorand-russia-walked-through-it-11547137112 (accessed May 11, 2020).
[wpedon id=”5868″ align=”center”]