NERC Coverup Investigation Report
NERC Coverup Introduction
“Publicity is justly commended as a remedy for social and industrial diseases. Sunlight is said to be the best of disinfectants; electric light the most efficient policeman.”
Justice Louis D. Brandeis
In an official assessment to the U.S. Congress released on January 29, 2019, the U.S. Intelligence Community confirmed that the U.S. electric grid is not secure against foreign incursions:[1]
Russia has the ability to execute cyber attacks in the United States that generate localized, temporary disruptive effects on critical infrastructure—such as disrupting an electrical distribution network for at least a few hours—similar to those demonstrated in Ukraine in 2015 and 2016. Moscow is mapping our critical infrastructure with the long-term goal of being able to cause substantial damage.
Vulnerability of the U.S. electric grid to foreign attack has been longstanding. In an April 8, 2009 article, “Electricity Grid in U.S. Penetrated By Spies,” the Wall Street Journal disclosed:[2]
Cyberspies have penetrated the U.S. electrical grid and left behind software programs that could be used to disrupt the system, according to current and former national-security officials.
The spies came from China, Russia and other countries, these officials said, and were believed to be on a mission to navigate the U.S. electrical system and its controls. The intruders haven't sought to damage the power grid or other key infrastructure, but officials warned they could try during a crisis or war.
"The Chinese have attempted to map our infrastructure, such as the electrical grid," said a senior intelligence official. "So have the Russians."
FERC’s decade-long failure to secure the U.S. electric grid is in large part due to its complicity in a North American Electric Reliability Corporation (NERC) enforcement regime that shields the identities of standard violators from outside scrutiny. The NERC coverup, enabled and abetted by FERC, started in July 2010. (Previous to July 6, 2010, identities of standards violators were disclosed by both NERC and FERC.) Under this apparently illegal enforcement regime, incentives for electric utilities have become clear: devote only moderate attention to grid security while knowing any gaps will be kept hidden from ratepayers, investors, the U.S. Congress, and the public at large.
Disclosure is the cornerstone of a successful regulatory scheme in a free society. The Securities and Exchange Commission routinely publicizes the names of companies and individuals subject to regulatory actions under U.S. securities laws;[3] the Food and Drug Administration routinely publicizes the names of companies whose food is being recalled due to public safety concerns;[4] the National Transportation Safety Board routinely publicizes the names of companies responsible for airplane crashes as well as the causes. There are numerous other examples of appropriate disclosure. [5] It is high irony that public disclosure has made food consumption and airline travel extremely safe for Americans while a far greater danger, the threat of long-term blackout for millions, has been neglected by the responsible federal regulator, FERC.
Presently, NERC, as the designated ERO, is improperly using the Critical Energy/Electric Infrastructure Information (CEII) rule[6] to hide from public view the identities of entities that violate Critical Infrastructure Protection (“CIP”) Reliability Standards – even when the violation has been abated and there is no longer a security need to withhold this information. Essentially, NERC and the Regional Entities are misusing FERC’s authority to shield industry from public scrutiny. The Commission must not allow this practice repugnant to the public interest to continue.
Duke Energy Example – FERC Docket NP19-4-000
On January 25, 2019, NERC filed a 250 page Notice of Penalty with FERC that disclosed 127 cybersecurity standard violations by an “unidentified registered entity.” NERC and its Regional Entities (RE) determined:
[T]he 127 violations collectively posed a serious risk to the security and reliability of the BPS (Bulk Power System). The Companies’ violations of the CIP Reliability Standards posed a higher risk to the reliability of the BPS because many of the violations involved long durations, multiple instances of noncompliance, and repeated failures to implement physical and cyber security protections.
The NERC-imposed fine was $10 million, tiny in comparison to Duke’s 2017 net income of $3 billion. It is notable that the Notice of Penalty revealed violations that could allow adversaries in remote locations to gain electronic access to grid facilities:
The REs determined that the Companies allowed interactive remote access to the BCSs (Bulk Electric System Cyber Systems) inside the Companies ESP (Electronic Security Perimeter) without first going through an Intermediate System, utilizing encryption, and requiring multi-factor authentication.
The violation started when the Standard became mandatory and enforceable and is currently ongoing. [Emphasis added.]
The violated standard, CIP-005-5-2 R2, became effective in July 2015. Without fear of public scrutiny, it is apparent that even three and one-half years have not been sufficient time for the “unidentified registered entity” to remedy this currently ongoing violation.
On February 1, 2019, trade publication EnergyWire disclosed that Duke Energy is the unnamed standards violator.[7] Duke Energy is one of America’s largest utilities, with 7.2 million customers across seven states. Duke’s generation fleet includes six nuclear plants. A physical or cyber attack on Duke could cause a long-term, wide-area blackout and result in release of radioactive contaminants. Nonetheless, the NERC standard enforcement regime, with its practice of hiding the names of violators under the guise of CEII, has failed to assure the protection of Americans depending on Duke for their electric power.
Pacific Gas and Electric Example – FERC Docket NP18-7-000
Another example of NERC abuse of the CEII rule is contained in FERC Docket NP18-7-000, which is hereby attached as Exhibits A-G. Also instructive are the events both before and after the docket. Let’s start with the end of the story – the American public is informed.
On August 24, 2018, the Wall Street Journal ran a story titled: “PG&E Identified as Utility That Lost Control of Confidential Information.” Subtitle: “As a result of 2016 failure, 30,000 records about PG&E’s cyber assets were exposed on the internet.”[8] This story stems from FERC Docket NP18-7-000, however, it required Herculean effort by citizens to force the disclosure of PG&E’s identity. This should not have been the case.
Events leading to FERC Docket NP18-7-000 began on May 30, 2016 when cybersecurity expert Chris Vickery reported a massive data breach by Pacific Gas and Electric (PG&E).[9] According to Mr. Vickery:
Among other things, it contained details for over 47,000 PG&E computers, virtual machines, servers, and other devices. All of it completely unprotected. No username or password required for viewing. We’re talking about IP addresses, operating systems, hostnames, locations, MAC addresses, and more. This would be a treasure trove for any hostile nation-state hacking group. That’s not to mention the 120 hashed employee passwords, or the plaintext NTLM, SOAP, and mail passwords.
Any anonymous internet user—including those in North Korea, Iran or Russia—having free access to sensitive PG&E data is a grave national security violation. A cyber-attack on PG&E could cause a cascading collapse, resulting in a blackout for San Francisco, Silicon Valley, and much of the Western Interconnection.
On February 28, 2018 NERC issued a “Notice of Penalty regarding Unidentified Registered Entity”[10] in which the NERC-anonymized entity apparently agreed to pay penalties of $2.7 million for very serious cybersecurity violations. According to NERC, this data breach involved “30,000 asset records, including records associated with Critical Cyber Assets (CCAs). The records included information such as IP addresses and server host names.”
According to NERC:
These violations posed a serious or substantial risk to the reliability of the bulk power system (BPS). The CCAs associated with the data exposure include servers that store user data, systems that control access within URE’s [Unidentified Regulated Entity’s] control centers and substations, and a supervisory control and data acquisition (SCADA) system that stores critical CCA Information. The data was exposed publicly on the Internet for 70 days. The usernames of the database were also exposed, which included cryptographic information of those usernames and passwords.
Exposure of the username and cryptographic information could aid a malicious attacker in using this information to decode the passwords. This exposed information increases the risk of a malicious attacker gaining both physical and remote access to URE's systems. A malicious attacker could use this information to breach the secure infrastructure and access the internal CCAs by jumping from host to host within the network. Once in the network, the attacker could attempt to login to CCAs, aided by the possession of username and password information.
By the time of NERC’s submission of its February 28, 2018 “Notice of Penalty regarding Unidentified Registered Entity,” the breach had been mitigated and there was no longer an access vulnerability.[11] According to a federal regulation, 18 CFR § 39.7 (b)(4), at the point where “Notice of Penalty regarding Unidentified Registered Entity” was submitted to FERC, the identity of the “URE” should have been disclosed.
NERC cannot argue that its February 28, 2018 “Notice of Penalty regarding Unidentified Registered Entity” should be a non-public proceeding related to a “cybersecurity incident”[12] as it does not meet the regulatory definition of a “cybersecurity incident.”[13] According to NERC, this incident was a not “malicious act” as the definition of “cybersecurity incident” requires – rather it was a colossal blunder on the part of the regulated entity. The public had the right to know who endangered them.
Despite the interventions and protests of several citizens and groups in Docket NP18-7-000[14], the matter was closed without review by the Commission on May 30, 2018[15] and the name of the “Unidentified Registered Entity” was never disclosed on NERC’s website or in FERC’s public docket.
Below is the information as it appears on NERC’s public website about FERC Docket NP18-7-000:[16]
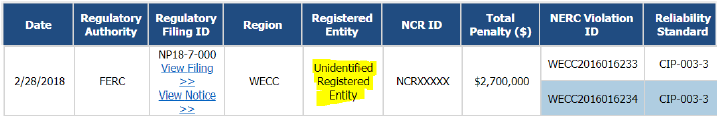
It took a Freedom of Information Act (FOIA) request by this Investigator, and an appeal of the denied request, to conclusively determine the identity of the standards violator: PG&E, one of America’s largest utilities.
Numerous Other Examples of Secret Enforcement Actions
In fact, analysis of NERC enforcement actions between 2010 and 2018 reveals a multitude of cases in which NERC hid the identities of the “registered entities” that violated reliability standards.[17] Many of these enforcement actions involved settlements for substantial penalties, yet the settlement agreements were not disclosed either.
Exhibit O Lists 243 FERC dockets and at least 1,465 “Unidentified Registered Entities” related to these dockets who violated CIP standards between 2010 and 2018. None of these “Unidentified Registered Entities” has yet been identified to the public by either NERC or FERC even though they have been subject to regulatory action overseen by the United States government. These actions all claim that the violations have been “mitigated,” so there is absolutely no national security argument that the identities of these entities and the settlement agreements should still be withheld from the public.
Moreover, NERC cannot argue – as they are attempting to argue in the January 25, 2019 Duke Energy NOP (Docket Number NP19-4-000) – that these should be non-public proceedings related to “cybersecurity incidents.” None of these 243 regulatory actions involve “cybersecurity incidents” as defined in the regulation. These dockets were regulatory actions resulting from audits or self-reports – not “a malicious act or suspicious event that disrupts, or was an attempt to disrupt, the operation of those programmable electronic devices and communications networks including hardware, software and data that are essential to the Reliable Operation of the Bulk-Power System” as defined at 18 CFR § 39.1. NERC is simply misapplying this FERC regulation in an attempt to shield the industry from proper public scrutiny.
A review of the publicly available information on these dockets reveals troubling issues; however, without the disclosure of the names of the entities and the text of settlement agreements, it is impossible for the public to fully appreciate how standards violations by utilities place lives at risk. Here are some examples:
- Since the Metcalf substation attack on PG&E on April 16, 2013, one would think that there would be utility focus on physical security for high voltage transformers – most of which are guarded only by a chain link fence and crossed fingers. So exactly how many enforcement actions would you guess there have been in the last 5 years for “CIP-014” physical security? Only one. (FERC Docket NP18-14-000.)
- Many of the “penalties” result from settlement agreements (e.g., the “Unidentified Registered Entity” agrees to pay the “penalty” and in many cases does not admit fault for the violation). Without knowing the details of the settlement agreements, the public cannot adequately analyze the terms and penalties, or even identify offending utilities.
- In some of the cases that were “settled,” the regulated entities were “uncooperative” (FERC Docket NP16-12-000) or “not fully transparent and forthcoming” (FERC Docket NP18-7-000). “Settling” with such bad actors raises many regulatory red flags and the public needs to analyze these FERC-approved transactions in more detail.
- I have found numerous examples of non-CIP violations that have been redacted. For example, I have found at least four violations of vegetation management standards for transmission lines in the Western Interconnection[18] – the same region where over 86 deaths occurred in the “Camp Fire” – the deadliest and most destructive wildfire in California history. This is the same region where a “regulated entity” (PG&E) has significant liability for wildfires. The public has a right to know who standard violators are, especially when the standards violations may have resulted in dozens of deaths.
After this NERC coverup started in July of 2010, there has been less incentive to fix the grid security problems. That’s why disclosure is important. Why should utilities spend money to fix grave cybersecurity issues if they know that 1) if caught, the friendly regulator will “settle” the violation privately and the settlement agreement will be kept secret, 2) the utility can negotiate a trivial fine, and 3) the utility’s name will not be disclosed to the public?
Federal Regulations Require Disclosure
18 CFR § 39.7 (b)(4) provides that: “Each violation or alleged violation shall be treated as nonpublic until the matter is filed with the Commission as a notice of penalty or resolved by an admission that the user, owner or operator of the Bulk Power System violated a Reliability Standard or by a settlement or other negotiated disposition.” [Emphasis added.]
Further, 18 CFR § 39.7(d)(1) provides that a notice of penalty by the Electric Reliability Organization shall consist of, inter alia: “The name of the entity on whom the penalty is imposed.”
The federal regulations are very clear that the name of the entity on whom the NERC penalty is imposed must be disclosed. Yet, somehow NERC has apparently been excused from complying from federal regulations. How has this happened?
Even the Commission’s own interpretation of the Critical Energy Infrastructure Information (CEII) rules support disclosure. I note that FERC Order No. 833 holds that the Commission’s practice is that information that “simply give[s] the general location of the critical infrastructure” or simply provides the name of the facility is not Critical Energy Infrastructure Information (CEII).[20]
Nevertheless, in July 2010 FERC began allowing NERC to hide the identity of the “Unidentified Registered Entities.” Further, as described below, NERC claims FERC instructed this change in policy.
NERC’s concealments are against the public interest and should never have been allowed by FERC. The PG&E data breach in 2016 and NERC’s cover-up of the identity of the “Unidentified Registered Entity” in FERC Docket NP18-7-000 — a standard violation by NERC’s own admission that endangered the bulk power system — is clearly against the public interest. Likewise for the NERC coverup of 127 cybersecurity violations of Duke Energy exposed by the press in January 2019. The public must be able to cast scrutiny over the activities of NERC and its regulated entities for the self-regulatory scheme codified in Section 215 of the Federal Power Act (16 U.S. Code § 824o) to be effective.
Disclosure of Violators’ Identity Should Be the Default Practice
In the PG&E example, disclosure of the identity of the “URE” took a Freedom of Information Act (FOIA) request and a subsequent appeal by this Investigator. Attached as exhibits are the initial request (Exhibit H), FERC’s April 23, 2018 submitter rights letter to NERC (Exhibit I), NERC’s April 30, 2018 Response Letter to FERC (Exhibit J), FERC’s May 25, 2018 response letter to me denying the FOIA request in its entirety (Exhibit K), my June 16, 2018 appeal of FERC’s determination (Exhibit L), FERC’s August 2, 2018 response letter granting my appeal in part – specifically agreeing to disclose the identity of the URE (Exhibit M), and the August 24, 2018 FERC disclosure of the requested information (Exhibit N).
Notably, FERC’s initial denial of the FOIA request on May 25, 2018 was based on NERC’s very puzzling interpretation of FERC’s policy. I am including NERC’s objection below in its entirety:
NERC is compelled to object to this FOIA Request, because the Federal Energy Regulatory Commission (“Commission”) has instructed NERC not to divulge the identity of entities that have violated NERC Critical Infrastructure Protection (“CIP”) Reliability Standards. The Commission’s expectation that NERC should not identify entities violating CIP Reliability Standards is longstanding but is most recently reflected in FERC’s 2014 Order on the Electric Reliability Organization’s Five-Year Performance Assessment. In that order, the Commission stated that, “[w]ith respect to concerns and questions raised regarding NERC’s protection of information deemed to be confidential, particularly as related to cybersecurity incidents or CIP violations, we believe that NERC currently has adequate rules and procedures in place to protect against improper disclosure of sensitive information (…).” Order on the Electric Reliability Organization’s Five-Year Performance Assessment, 149 FERC ¶61,141, at n. 55, P 47, and n. 65 (2014) (in response to a commenter referencing a prior inadvertent disclosure of the identity of a URE sanctioned for violations of CIP Reliability Standards). [Emphasis added.]
The statement that “the Federal Energy Regulatory Commission (‘Commission’) has instructed NERC not to divulge the identity of entities that have violated NERC Critical Infrastructure Protection (‘CIP’) Reliability Standards” is completely unsupported by any reasonable read of 149 FERC ¶61,141. This order simply does not state or imply in any way that the Commission has ever given NERC any such instruction. And, to the extent that the NERC Rules of Procedure conflict with 18 CFR § 39.7, the federal regulation must take precedence. A corporation’s “procedures” do not trump federal regulations.[21]
While this slight of pen on the part of NERC’s attorneys may have mislead the Commission’s staff into denying the initial FOIA request on May 25, 2018 (Exhibit D), on appeal, the Commission’s general counsel correctly concluded “that the name of the URE can be disclosed” on August 2, 2018 (Exhibit F).
However, this one FOIA disclosure in this one instance is not enough to abate NERC’s abhorrent practice of routinely concealing information from the public – which continues to this day. FERC regulations, while seemingly clear, have been abused by NERC and the Regional Entities to the point of creating a “new normal.” Clarification by means of a formal rulemaking is needed.
FERC’s Mandate to Act in the Public Interest
16 U.S.C. § 824o(d)(2) provides that: “The Commission may approve, by rule or order, a proposed reliability standard or modification to a reliability standard if it determines that the standard is just, reasonable, not unduly discriminatory or preferential, and in the public interest.” [Emphasis added.]
Thus, FERC is charged with serving the public interest. Not the interests of NERC and/or the electric utility industry. The public interest demands that information on industry practices, successes, failings and regulatory actions be available for public scrutiny. This is especially the case in the electric utility industry on which every American is dependent – and indeed, pays for.
In order to serve the public interest, the Commission should not allow NERC and the electric utility industry to continue to hide the identities of regulated entities that are subject to regulatory actions.
Conclusion
Continuing assessments by the U.S. intelligence community make it clear that our electric grid is not secure. By allowing NERC to hide the identities of utilities that violate grid security standards, FERC is failing in its duty to the American public. Free of public scrutiny, utilities do not correct security shortfalls for months and even years; the regulatory system is broken. Now is the time to end NERC’s apparently illegal scheme that hides the names of the violators of grid security standards.
Exhibits (Click Here - Large File):
- February 28, 2018 NERC Full Notice of Penalty regarding Unidentified Registered Entity
- March 30, 2018 FERC Notice (162 FERC ¶ 61,291)
- April 15, 2018 Motion to Intervene of Michael Mabee
- April 15, 2018 Motion to Intervene and Comment of Public Citizen, Inc. and The Utility Reform Network
- May 29, 2018 Comments of Isologic, LLC and the Foundation for Resilient Societies
- May 29, 2018 Comments of Frank J. Gaffney
- May 30, 2018 FERC Notice (163 FERC ¶ 61,153)
- April 13, 2018 FOIA Request (FOIA No. FY18‐75)
- April 23, 2018 FERC Submitter Rights Letter to NERC
- April 30, 2018 NERC Response Letter to FERC
- May 25, 2018 FOIA Response Letter
- June 16, 2018 Appeal of Determination in FOIA No. FY18‐75
- August 2, 2018 FERC Response Letter
- August 24, 2018 FERC Response Letter
- 246 FERC Dockets involving "Unidentified Registered Entities" 2010-2018
Footnotes
[1] Coats, Daniel R. “Worldwide Threat Assessment of the U.S. Intelligence Community” Senate Select Committee on Intelligence. January 29, 2019. https://www.dni.gov/files/ODNI/documents/2019-ATA-SFR---SSCI.pdf (accessed February 5, 2019). [2] Gorman, Siobhan. “Electricity Grid in U.S. Penetrated By Spies.” Wall Street Journal. April 8, 2009. https://www.wsj.com/articles/SB123914805204099085 (accessed February 5, 2019). [3] U.S. Securities and Exchange Commission. https://www.sec.gov/news/pressreleases (accessed November 22, 2018). [4] U.S. Food and Drug Administration. https://www.foodsafety.gov/recalls/recent/index.html (accessed November 22, 2018). [5] U.S. National Transportation Safety Board. https://www.ntsb.gov/investigations/AccidentReports/Pages/AccidentReports.aspx (accessed February 5, 2019). [6] 18 CFR § 388.113, et seq. [7] Sobczak, Blake and Behr, Peter. “Duke agreed to pay record fine for lax security — sources” E&E News, February 1, 2019. https://www.eenews.net/energywire/2019/02/01/stories/1060119265?fbclid (accessed February 5, 2019). [8] Smith, Rebecca. “PG&E Identified as Utility That Lost Control of Confidential Information.” The Wall Street Journal. August 24, 2018. https://www.wsj.com/articles/pg-e-identified-as-utility-that-lost-control-of-confidential-information-1535145850 (accessed November 22, 2018). [9] Vickery, Chris. “Pacific Gas and Electric Database Exposed.” https://mackeeper.com/blog/post/231-pacific-gas-and-electric-database-exposed (accessed November 28, 2018). [10] Attached as Exhibit A. [11] Id. At 4-5. [12] 18 CFR § 39.7(e)(7) [13] 18 CFR § 39.1 defines “cybersecurity incident” as “a malicious act or suspicious event that disrupts, or was an attempt to disrupt, the operation of those programmable electronic devices and communications networks including hardware, software and data that are essential to the Reliable Operation of the Bulk Power System.” [14] Attached as Exhibits C-F. [15] 163 FERC ¶ 61,153, attached as Exhibit G. [16] https://www.nerc.com/pa/comp/CE/Pages/Actions_2018/Enforcement-Actions-2018.aspx (accessed December 9, 2018) [17] 2014: https://www.nerc.com/pa/comp/CE/Pages/Actions_2014/Enforcement-Actions-2014.aspx;2015: https://www.nerc.com/pa/comp/CE/Pages/Actions_2015/Enforcement-Actions-2015.aspx;
2016: https://www.nerc.com/pa/comp/CE/Pages/Actions_2016/Enforcement-Actions-2016.aspx;
2017: https://www.nerc.com/pa/comp/CE/Pages/Actions_2017/Enforcement-Actions-2017.aspx;
2018: https://www.nerc.com/pa/comp/CE/Pages/Actions_2018/Enforcement-Actions-2018.aspx (accessed December 9, 2018).
[18] See FERC Docket Numbers: NP11-1-000; NP11-128-000; NP11-137-000 and NP12-20-000. [20] FERC Order No. 833 at pg. 17. Also see 18 C.F.R. §388.113(c)(1)(iv). [21] Perhaps FERC or one of its Commissioners gave an “off-the-record” instruction to NERC to conceal the identity of standards violators. If NERC continues to claim an exemption from 18 CFR § 39.7 in future filings, this is a matter that should be investigated by the Department of Energy’s Office of the Inspector General.Further Information on NERC Coverup:
- Click here to read my report to the Senate
- Click here to read my report to FERC
- Download List of “Unidentified Registered Entity” Dockets
- Click here to read my December 2018 FOIA Request
- Click here to read my January 2019 FOIA Request
Related NERC Coverup Reports:
- Dear Senators Murkowski and Manchin…
- Transmission Vegetation Management Cover Up?
- FERC Commissioner Cheryl LaFleur: Step Up on Grid Security or Step Down!
- Electric Grid Cyber Cover-Up: More Details Emerging
- These “Unidentified Registered Entities” Endangered the Electric Grid
- PG&E endangered the grid – and tried to cover it up
- The Electric Utility Industry Lacks Effective Regulation
- Now It’s a FERC Cover-Up
- A NERC Cover-Up? Who Put the Electric Grid at Risk?
- Grid Cybersecurity: The Critical Infrastructures Are Under Attack
NERC Coverup Investigation Report
