Electric Grid Cyber Cover-Up: More Details Emerging
.
.
More Details Emerging on the Electric Grid Cyber Cover-Up
The deeper we dive into the electric grid cyber cover-up, the more disturbing it becomes. In the last 5 years (2014-2018), there have been 53 Federal Energy Regulatory Commission (FERC) dockets involving 81 “Unidentified Registered Entities.” These all allege violations of Critical Infrastructure Protection Standards (CIP Standards). Such violations could endanger the electric grid, however, the identities of the violators are being kept from the public. Here is a comprehensive list of the CIP violations with some data on each one. CLICK HERE FOR LIST.
There is a lot to digest.
First of all, none of the violators are identified. The North American Electric Reliability Corporation (NERC) has created a loophole whereby they bend the regulations to “protect the guilty” so that these companies do not have to be embarrassed. They are all simply called “Unidentified Registered Entities” or “UREs.” And FERC has allowed this to happen.
Next, each violation has a “Violation Risk Factor” and a “Violation Severity Level.” These seem to be somewhat subjective and it is not easy to find and compare this information. According to NERC:
“A Violation Severity Level (VSL) is a post-violation measurement of the degree to which a Reliability Standard Requirement was violated (Lower, Moderate, High, or Severe). To establish a Base Penalty for a violation, NERC considers the VSL, together with a Violation Risk Factor, which represents the potential risk to reliability.”
So they are supposed to consider both the “Violation Severity Level” and the “Violation Risk Factor.” This is not easy for the public to audit because the information is hard to find and only exists in a form that makes analysis difficult. Is this by design? I wonder.
Also, many of the “penalties” result from settlement agreements (e.g., the “URE” agreed to pay the “penalty” and in many cases do not admit fault for the violation. How convenient).
Clearly, something smells very foul in a regulatory system where the public does not have access to information about regulatory actions which are approved by the United States government – FERC has to at least passively rubber-stamp all of these actions.
It’s bad enough that we have an electric grid cyber cover-up, but when you look at some of these “enforcement actions”, it paints a very weak regulatory picture.
Physical Security? Nope.
Here’s one example. Since the Metcalf transformer attack on April 16, 2013, you would think that there would be some focus on physical security of the high voltage transformers – most of which are guarded by a chain link fence and crossed fingers. So exactly how many enforcement actions would you guess there have been in the last 5 years for “CIP-014” physical security? Only one. (FERC Docket NP18-14-000.) How can this possibly be? Moreover, this is very difficult to see if you are a member of the public due to the electric grid cyber cover-up .
Some Bad Actors
There are a lot of substantial fines here, but two fines are bigger than the others.
We know that PG&E Corp (identified by a Freedom of Information Act request) was fined $2.7 million dollars in Docket NP18-7-000. a great quote from that one is:
“URE was not fully transparent and forthcoming with all pertinent information detailing the data exposed in the incident. Specifically, URE did not provide WECC initially with all the data fields exposed in the incident”
In other words, they lied.
Another interesting one is the $1,700,000 fine of an “Unidentified Registered Entity” announced on February 29, 2016 – FERC Docket NP16-12-000.
“URE was not cooperative throughout the compliance enforcement process, and ReliabilityFirst considered URE’s lack of cooperation as an aggravating factor in the penalty determination.”
and
“ReliabilityFirst considered 21 of the instant violations as repeat noncompliance with the subject NERC Reliability Standards…”
Self regulation at its best. I would note that both of these “big fines” (actually, quite paltry when you consider the risk that these violations exposed us all to) were settlement agreements. In other words, these already uncooperative and not so forthcoming entities agreed to pay these fines. Doesn’t seem like they hurt too much. And they still get to be an “URE” and not have their name revealed to the public!
As you know, we have filed a Freedom of Information Act (FOIA) request with FERC for the identities of these “Unidentified Registered Entities” – stay tuned as this battle unfolds.
CLICK HERE FOR THE LIST OF “Unidentified Registered Entities”
How to Read the Electric Grid Cyber Cover-Up Chart
I’m including a list and links below to the CIP standards (as of 12/31/2018) – there are also links on the electric grid cyber cover-up document. If you need a primer on what the electric grid is and how it is regulated, click here.
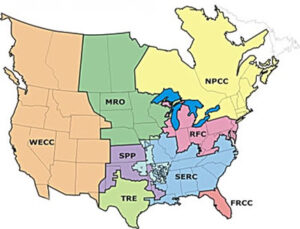
Regions. NERC delegates its enforcement authority to regional entities. So, on the chart under “Region” you will see the initials for one of the below regional entities. The map helps narrow down the geographic area.
- Florida Reliability Coordinating Council (FRCC)
- Midwest Reliability Organization (MRO)
- Northeast Power Coordinating Council (NPCC)
- ReliabilityFirst Corporation (RFC)
- SERC Reliability Corporation (SERC)
- Southwest Power Pool RE (SPP)
- Texas Reliability Entity (TRE)
- Western Electricity Coordinating Council (WECC)
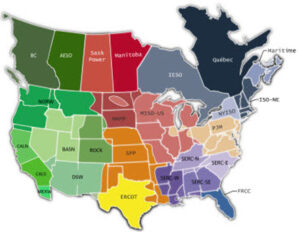
In addition to the regional entities, the new NERC reliability assessment areas are a mixture of NERC reliability entities, entity sub-regions, regional transmission organizations and system operators. The map below illustrates these:
- BASN – Basin (WECC)
- CALN– California – North (WECC)
- CALS – California – South (WECC)
- DSW– Desert Southwest (WECC)
- ERCOT – Electric Reliability Organization of Texas (TRE)
- FRCC – Florida Reliability Coordinating Council
- ISO-NE – ISO New England Inc (NPCC)
- MAPP – Mid-Continent Area Power Pool
- MISO – Midwest Independent Transmission System Operator, Inc
- NORW – Northwest (WECC)
- NYISO – New York Independent System Operator (NPCC)
- PJM – PJM Interconnection
- ROCK – Rockies (WECC)
- SERC-E – SERC – East
- SERC-N – SERC – North
- SERC-SE – SERC – Southeast
- SERC-W – SERC – West
- SPP – Southwest Power Pool Regional Entity
Each violation has a “Violation Risk Factor” listed. You have to dig and find the “Violation Severity Level” to get the full picture (although the categories seem rather subjective). You also have to dig through multiple layers of documents to find the information I cobbled together on this chart. It contains both the “Violation Risk Factor” and “Violation Severity Level” side by side. Normally, one has to do a “NERC treasure hunt” to find this information piece by piece. This is the first time this information has been compiled in one place for analysis.
Several of us from the Secure the Grid Coalition are actively analyzing and working this issue. Subscribe to my blog to stay informed of our progress.
###
Download Electric Grid Cyber Cover-Up Chart
Download Underlying Regulatory Filings (Huge 11 MB File)
Subscribe to my blog for updates:
[email-subscribers namefield=”YES” desc=”” group=”Public”]
CIP standards (as of 12/31/2018)

Title: Electric Grid Cyber Cover-Up