NERC’s “Cybersecurity Incident” Shell Game
(Or: The Electric Grid Thinks We Are All Stupid)
Consider this: The North American Electric Reliability Corporation (NERC) reported ZERO “Cybersecurity Incidents” for the last three years. But NERC is withholding the names of cyber violators from the public because of the “Cybersecurity Incidents” over the last three years.
Just let that sink in for a minute.
This is one of several flawed arguments that NERC – the self regulator of the electric grid – uses to try to justify covering up the identities of companies that have violated Critical Infrastructure Protection (CIP) standards since 2010. (Click here to read an in depth report on the coverup.)
So, not only does literally everybody in the U.S. pay an electric bill; not only do we all rely on the electric grid for everything necessary for life – but it seems the electric grid also thinks we are all stupid.
Seriously, here is the issue: Secret self-regulation does not work.
The electric grid is self regulated by NERC – a non-profit corporation. This self-regulatory scheme is nominally overseen by the Federal Energy Regulatory Commission (FERC). For the last decade, Russian and Chinese hackers have been inside the U.S. electric grid. Our regulators have failed and refused to secure the electric grid. This shocking revelation was front and center when Senator Angus King (Maine) questioned the CEO of NERC, James Robb, on February 14, 2019:
Despite the fact that we have known for a decade that the Russians and Chinese have penetrated the electric grid little has been done. (Read this Wall Street Journal article from 10 years ago, or Click Here for a video of the April 8, 2009 report for those who don’t have a WSJ subscription.)
Disclosure is the cornerstone of a successful regulatory scheme in a free society. The Securities and Exchange Commission routinely publicizes the names of companies and individuals subject to regulatory actions under U.S. securities laws; the Food and Drug Administration routinely publicizes the names of companies whose food is being recalled due to public safety concerns; the National Transportation Safety Board routinely publicizes the names of companies responsible for airplane crashes. There are numerous other examples of appropriate disclosure. It is high irony that public disclosure has made food consumption and airline travel extremely safe for Americans while a far greater danger – the threat of long-term blackout for millions – has been neglected by the responsible federal regulator, FERC.
The Secure The Grid Coalition is fighting to fix the electric grid’s broken regulatory scheme that is endangering all of us. The fight is shaping up around the issue of a $10 million penalty NERC imposed on January 25, 2019 against unnamed companies that committed 127 violations of Critical Infrastructure Protection (CIP) standards over several years. The press has since outed Duke Energy Corp as the violator, but neither NERC nor the U.S. government have acknowledged this. The coverup remains.
You can join us and be heard!
We need to all let the Federal Energy Regulatory Commission (FERC) know that the security of the electric grid is critical – secret regulation and coverups are unacceptable to the public. As a citizen, you have the right to file a “Motion to Intervene” in this docket and be heard! The deadline to file on this docket is August 30, 2019 so write your letter today and submit it online to FERC Docket Number NP19-4-000, or mail it in to FERC (Be sure to include the Docket Number in your letter).
Submit to FERC online HERE (you need to register if this is your first time)
or, submit by mail:
Federal Energy Regulatory Commission
Kimberly D. Bose, Secretary
ATTN: Docket No. NP19-4-000
888 First Street, NE
Washington, DC 20426
- Click Here for Background Information on the Coverup
- Click Here for Notice of Penalty in Docket NP19-4-000 (large file)
- Click Here for Motion to Intervene of Michael Mabee
- Click Here for Motion to Intervene of Public Citizen, Inc.
- Click Here for Motion to Intervene of Dale Rowley #1
- Click Here for Motion to Intervene of Dale Rowley #2
- Click here for Motion to Intervene of Karen Testerman
- Click here for Motion to Intervene of Foundation for Resilient Societies
- Click here for Motion to Intervene of Dr. Fred Reitman
- Click here for Motion to Intervene of George R Cotter, Esq.
- Click here for Motion to Intervene of Henry W Newton
- Click here for Motion to Intervene of David K Testerman
- Click here for Motion to Intervene of Frank Gaffney
- Click here for Reply Comments of Foundation for Resilient Societies
- Click here for Reply Comments of Michael Mabee
- Click here for Motion to Intervene of Douglas E. Ellsworth
- Click here for 2nd Motion to Intervene of George R. Cotter, Esq.
- Click here for Motion to Intervene of Kenneth D. Chrosniak
Michael Mabee, a private citizen, requests the Commission’s leave to intervene in the above captioned docket, pursuant to 18 C.F.R. § 39.7(e)(4). I request that 1) the Commission review this Notice of Penalty (NOP) to ensure that it is in the public interest, and 2) that the name of the entities(s), the unredacted Notice of Penalty and the unredacted settlement agreement be released in the public docket. NERC has made redactions to the publicly available documents, alleging the identities and other identifying information about Critical Infrastructure Protection (CIP) standards violators must be kept from the public. The lack of transparency in this Notice of Penalty raise significant public interest concerns.
Background on FERC Docket No. NP19-4-000
On January 25, 2019, the North American Electric Reliability Corporation (NERC) filed a Notice of Penalty with FERC that disclosed 127 cybersecurity standard violations by unidentified “Companies.”[1] NERC and its Regional Entities (RE) determined:
[T]he 127 violations collectively posed a serious risk to the security and reliability of the BPS (Bulk Power System). The Companies’ violations of the CIP Reliability Standards posed a higher risk to the reliability of the BPS because many of the violations involved long durations, multiple instances of noncompliance, and repeated failures to implement physical and cyber security protections.
It is notable that the Notice of Penalty revealed violations that could allow adversaries in remote locations to gain electronic access to grid facilities:
The REs determined that the Companies allowed interactive remote access to the BCSs (Bulk Electric System Cyber Systems) inside the Companies ESP (Electronic Security Perimeter) without first going through an Intermediate System, utilizing encryption, and requiring multi-factor authentication.
The violation started when the Standard became mandatory and enforceable and is currently ongoing. [Emphasis added.]
The violated standard, CIP-005-5-2 R2, became effective in July 2015. Without the violator having fear of public scrutiny, it is apparent that even three and one-half years have not been sufficient time for “the Companies” to remedy this currently ongoing violation.
On February 1, 2019, trade publication EnergyWire disclosed that Duke Energy is the unnamed standards violator.[2] Duke Energy is one of America’s largest utilities, with 7.2 million customers across seven states. Duke’s generation fleet includes six nuclear plants. A physical or cyber-attack on Duke could cause a long-term, wide-area blackout and result in release of radioactive contaminants. Nonetheless, the NERC standard enforcement regime, with its practice of hiding the names of violators under the guise of so-called Critical Energy/Electric Infrastructure Information (CEII), has failed to assure the protection of Americans depending on Duke for their electric power.
The NERC-imposed fine was $10 million, tiny in comparison to Duke’s 2017 net income of $3 billion.
This NOP had redactions that are far beyond the redactions in all previous CIP NOP’s submitted to FERC by NERC. For example, in all previous CIP NOPs, the identity of the Regional Entity (RE) was disclosed and the NERC Violation ID was disclosed. Also, in this NOP the reason for the NOP was redacted – usually it is disclosed that the reason the NOP is being filed is that, for example, the Regional Entity and the “Unidentified Registered Entity” have entered into a settlement agreement. Here on page 1 of the Duke NOP, NERC has redacted the reason for the NOP’s submission:

This is the first instance since 2010 that NERC has used this type of redaction. Also, the “NERC Violation ID” is redacted for the first time since 2010. Here is the beginning of the violation table from page 2 of the NOP:
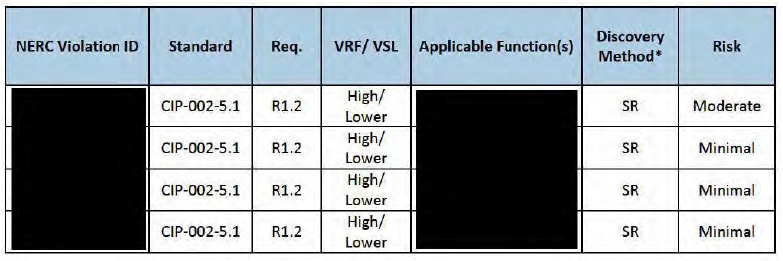
NERC’s coverup of the identity of the violator (‘the Companies”), the identity of the regulator (the “Regional Entities” or “REs”), and settlement agreement are profoundly against the public interest. FERC should not tolerate this concealment by NERC. “The Companies” were subjected to a $10-million fine for 127 cybersecurity violations; the details of this compliance gap are of great public interest.[3] The public must be able to cast scrutiny over the activities of NERC and its regulated entities for the self-regulatory scheme codified in Section 215 of the Federal Power Act to be effective.
Federal Regulations Require Disclosure
NERC requests that the redacted portions of the NOP be designated as nonpublic under 18 CFR § 39.7(b)(4) and as CEII under 18 CFR § 388.113(e)(1). Neither of these regulations provide NERC, the “Regional Entities” or “the Companies” relief from public scrutiny in this regulatory action. As described in detail below, NERC is apparently violating its duties as the designated “Electric Reliability Organization” (ERO) by:
- Improperly classifying information as CEII,
- Improperly applying the “Cybersecurity Incident” exemption to disclosure,
- Improperly applying the “disposition” exemption to disclosure,
- Providing misleading interpretations of Commission orders.
18 CFR § 39.7 (b)(4) provides that:
Each violation or alleged violation shall be treated as nonpublic until the matter is filed with the Commission as a notice of penalty or resolved by an admission that the user, owner or operator of the Bulk Power System violated a Reliability Standard or by a settlement or other negotiated disposition. The disposition of each violation or alleged violation that relates to a Cybersecurity Incident or that would jeopardize the security of the Bulk-Power System if publicly disclosed shall be nonpublic unless the Commission directs otherwise. [Emphasis added.]
Further, 18 CFR § 39.7(d)(1) provides that a notice of penalty by the Electric Reliability Organization shall consist of, inter alia: “The name of the entity on whom the penalty is imposed.”
So, 18 CFR § 39.7 (b)(4) and 18 CFR § 39.7(d)(1) are clear that at the point when “the matter is filed with the Commission as a notice of penalty or resolved by an admission that the user, owner or operator of the Bulk Power System violated a Reliability Standard or by a settlement or other negotiated disposition” then the name of the penalized entity as well as the supporting documentation – including the settlement agreement – must be publicly disclosed. Importantly, the “notice of penalty” is afforded different treatment in 18 CFR § 39.7 (b)(4) than the “disposition of each violation”—there is no provision in regulation to make the “notice of penalty” nonpublic. Moreover, 18 CFR § 39.7(d)(1) makes it absolutely clear that “the name of the entity on whom the penalty is imposed” is part of the “notice of penalty.”
18 CFR § 39.7 (b)(4) allows the “disposition of each violation” (or alleged violation) to be made nonpublic, but only if disclosure of the “disposition” would jeopardize security of the Bulk Power System. Again, the “name of the entity” is not part of “disposition” of the violation, so there is never an exemption of the violator’s name from public disclosure. Nor has NERC made a credible case that disclosure of the “disposition” of the Duke violations would jeopardize the security of the Bulk-Power System, especially when the violations do not involve bona fide Cybersecurity Incidents as defined in 18 CFR § 39.1.
FERC has made no public order (or change in regulation) to allow NERC to withhold the “notice of penalty” for the Duke NOP (or any other NOP). If FERC has made a private directive to NERC to withhold the “disposition” of the violations in Duke NOP, and other NOPs, then the public interest demands that the text of this hidden FERC directive and its underlying legal rationale be promptly released by the Commission.
NERC’s “Cybersecurity Incident” Shell Game.
The “cybersecurity incident” exception that NERC frequently evokes as a justification for covering up the names of violators clearly does not apply. It is critical to point out that nothing in this redacted NOP refers to a “cybersecurity incident.” 18 CFR § 39.1 defines “cybersecurity incident” as:
Cybersecurity Incident means a malicious act or suspicious event that disrupts, or was an attempt to disrupt, the operation of those programmable electronic devices and communications networks including hardware, software and data that are essential to the Reliable Operation of the Bulk-Power System.
There is no allegation in the NOP of a malicious act or suspicious event that disrupted or attempted to disrupt the Reliable Operation of the Bulk-Power System. This was simply a regulatory action after instances of noncompliance of CIP standards were discovered, either through self-reports or regulatory audits.
It is extremely disconcerting that NERC claims in 2015, 2016, and 2017 there were zero reportable cybersecurity incidents. In NERC’s June 2018 “State of Reliability 2018” report[4], on page 39 we see NERC’s claim:
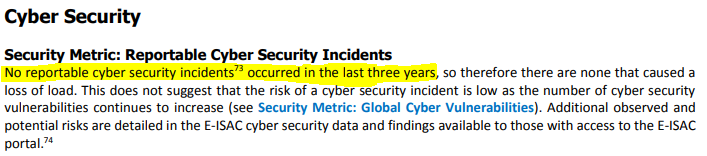
Yet somehow, in the Duke NOP NERC claims the name of “the Companies” must be withheld from public scrutiny since these are “cybersecurity incidents.” Since the violations described in the Duke NOP occurred over the same time period that NERC reported that there were no reportable “cybersecurity incidents”, the public is confused. Why is it we cannot have the name of the violator? In its State of Reliability report NERC says that there were no reportable cybersecurity incidents, but the Duke NOP contains descriptions of “cybersecurity incidents” so serious they must be redacted? NERC’s twisted logic defies all commonsense.
Further, to the extent that NERC attempts to argue that disclosure of the name of the regulated entity or the settlement agreement “would jeopardize the security of the Bulk-Power System if publicly disclosed”[5], their argument falls flat. In fact, it is misleading.
In the NOP NERC quotes FERC Order 672 – out of context – and argues that:
As the Commission has previously recognized, information related to CIP violations and cyber security issues, including the identity of the registered entity, may jeopardize BPS security, asserting that “even publicly identifying which entity has a system vulnerable to a ‘cyber attack’ could jeopardize system security, allowing persons seeking to do harm to focus on a particular entity in the Bulk-Power System.”[6]
This is a grossly selective use of a quote from FERC Order 672. The entire passage from the FERC order explains the benefit of transparency:
As explained in the NOPR, and confirmed by numerous commenters, a proceeding involving a Cybersecurity Incident requires additional protection because it is possible that Bulk-Power System security and reliability would be further jeopardized by the public dissemination of information involving incidents that compromise the cybersecurity system of a specific user, owner or operator of the Bulk-Power System. For example, even publicly identifying which entity has a system vulnerable to a “cyber attack” could jeopardize system security, allowing persons seeking to do harm to focus on a particular entity in the Bulk-Power System. While the Commission recognizes the benefit of transparency in Commission proceedings, as discussed by APPA and TAPS, the benefits of transparency are overridden in the limited situation of cases in which such transparency would jeopardize Bulk-Power System security. [Internal footnotes omitted, Emphasis added.]
Nothing in this NOP credibly alleges that a “Cybersecurity Incident” as defined in 18 CFR § 39.1 has taken place. Moreover, NERC provides no evidence or argument, other than a conclusory statement, that disclosure of the redacted information would jeopardize Bulk-Power System security.
Then NERC compounds this apparent misrepresentation by stating:
Consistent with the Commission’s statement, NERC is treating as nonpublic the identity of the Companies and any information that could lead to the identification of the Companies.[7]
In other words, NERC is blaming FERC for the coverup by quoting this out of context passage and apparently misapplying federal regulations.
If NERC has direction from FERC allowing redaction of Notices of Penalty, the public interest demands that FERC release the text of this direction. If in fact there is no direction from FERC, the Commission should make this clear.
Perhaps NERC is somehow arguing that releasing any data that identifies any entity that is subject to a regulatory action (or even the identity of the regulator or “Regional Entity”) will endanger the Bulk-Power System. One way to read this argument is is that since our regulatory regime is so weak and ineffective, a coverup is necessary so the “malicious actors” don’t find out how vulnerable we are.
Newsflash: Our enemies already know.[8]
NERC’s Abuse of the CEII Rule.
Presently, NERC as ERO, is improperly using the Critical Energy/Electric Infrastructure Information (CEII) rule[9] to hide from public view the identities of entities that violate Critical Infrastructure Protection (“CIP”) Reliability Standards – even when the violation has been abated and there is no arguable security need to withhold this information. Essentially, NERC and the Regional Entities are misusing FERC’s authority to shield industry from public scrutiny. The Commission must not allow this practice repugnant to the public interest to continue.
Only NERC is asserting that this information is CEII or “privileged” or “nonpublic” – the Commission has not made such a determination. 18 CFR § 388.112(c)(1)(i) Provides that:
The documents for which privileged treatment is claimed will be maintained in the Commission’s document repositories as non-public until such time as the Commission may determine that the document is not entitled to the treatment sought and is subject to disclosure consistent with § 388.108. By treating the documents as nonpublic, the Commission is not making a determination on any claim of privilege status. The Commission retains the right to make determinations with regard to any claim of privilege status, and the discretion to release information as necessary to carry out its jurisdictional responsibilities. [Emphasis added.]
NERC has for years been classifying the names of the violators and the settlement agreements as “nonpublic” and tries to argue that FERC also deems these documents as “nonpublic” – not so according to the regulations.
Finally, even the Commission’s own interpretation of the Critical Energy Infrastructure Information rules support disclosure. I note that FERC Order No. 833 holds that the Commission’s practice is that information that “simply give[s] the general location of the critical infrastructure” or simply provides the name of the facility is not Critical Energy Infrastructure Information (CEII).[10]
The NERC Enforcement Regime is Broken and Endangers the U.S.
CIP regulations should protect the U.S. electric grid by holding “the Companies” accountable to protect the portion of the U.S. critical infrastructure that they own or operate. Instead, NERC has twisted this regulatory scheme into a sham where companies have no incentive to do more than the minimum. If caught violating a CIP standard, NERC and the Regional Entities will settle the matter privately with “the Companies,” negotiating a “penalty” that “the Companies” are willing to pay and will keep the matter from public view. A great deal for “the Companies” – not so much for the American people.
NERC’s view of how an effective enforcement regime should work is gravely flawed. NERC essentially argues in the NOP that they are redacting the names of “the Companies” and any identifying information because:
Malicious individuals already target the Companies’ operational personnel, seeking bits and pieces of data to map the Companies’ systems and identify possible attack vectors. The public disclosure of a single piece of redacted information may not, on its own, provide everything needed to exploit an entity and attack the electric grid. But, successive public disclosures of additional pieces of redacted information will increase the likelihood of a cyber-intrusion with a corresponding adverse effect on energy infrastructure. Each successive disclosure could fill in some knowledge gaps of those planning to do harm, helping to complete the maps of entity systems. Therefore, it is important to examine and evaluate the redacted information in the aggregate.[11]
This is a generic argument that any information of any kind identifying “the Companies” would assist hackers. Therefore, according to NERC, hiding the names of the companies will somehow thwart the Chinese and Russian hackers.
What would work better is if “the Companies” took the CIP regulations seriously and put effort in to thwart the malicious individuals. What would also help is if NERC became a regulator rather than an industry advocate. Public scrutiny of regulatory failings is the time-tested method to ensure accountability in a free society.
NERC has been redacting the names of the companies since July 6, 2010 – over 8 ½ years. In an official assessment to the U.S. Congress released on January 29, 2019, the U.S. Intelligence Community confirmed that the U.S. electric grid is not secure against foreign incursions:[12]
Russia has the ability to execute cyber attacks in the United States that generate localized, temporary disruptive effects on critical infrastructure—such as disrupting an electrical distribution network for at least a few hours—similar to those demonstrated in Ukraine in 2015 and 2016. Moscow is mapping our critical infrastructure with the long-term goal of being able to cause substantial damage.
Redacting the names, NRC ID and other “identifying information” clearly hasn’t thwarted our adversaries – it has only thwarted the American people from evaluating the weakness of NERC’s enforcement regime – and actually it is this weak enforcement of CIP standards that has assisted the “malicious individuals.” (One has to wonder whether NERC is spending more legal effort on hiding threats from the public than on enforcing grid security standards on utilities.)
Finally, NERC has no problem providing all this identifying information on its website on all active registered entities in its “NERC Active Compliance Registry Matrix” (NCR). Exhibit A is the most recent list of all the 1495 registered entities – with NRC ID and functions – pieces of information redacted in the NOP – and in all other NOP’s since July 6, 2010. I obtained this list from NERC’s public website on February 10, 2019.[13] So this list apparently poses no information of interest to “malicious individuals” but somehow NERC argues that the name of the of the entity subjected to a regulatory action in every single CIP violation since July of 2010 somehow poses such a threat.
Industry Embarrassment Does Not Equal National Security Concern
Since NERC began covering up the names of CIP violators – as they are continuing to do in this NOP – there has been less incentive to fix the grid security problems. That’s why disclosure is important. Why should utilities spend money to fix grave cybersecurity issues if they know that 1) if caught, their friendly regulator will “settle” the violation privately and the settlement agreement will be kept secret, 2) the utility can negotiate a trivial fine, and 3) the utility’s name will not be disclosed to the public?
On the surface, it is hard to understand why the industry has taken the lack of transparency approach to CIP regulation. However, upon closer historical examination, the industry has crafted its own favorable (to the industry) regulatory scheme whereby it implements whatever protections are convenient and inexpensive – but it can avoid any protections that the industry deems too “burdensome.”[14] Simply put, the security of the electric grid is apparently optional – we depend on about 1,500 electric utility industry entities to do the right thing – but there is no strong requirement that they do the right thing.
A logical conclusion one can draw from this set of facts is that the industry seeks to avoid public exposure for their inaction on cyber security. Under the guise of protecting us (because we the public cannot be trusted with this sensitive information) private, secret regulation is ongoing, with back-room settlements and handshake penalties. Thus, “the Companies” and their shareholders avoid the embarrassment of being outed for a lack of action on Critical Infrastructure protection (CIP) standards. And NERC is not held accountable for their ineffective enforcement regime.
Meanwhile, after a decade of inaction, it is well known that our electric grid is vulnerable – and in fact, has been penetrated and probed. This regulatory scheme has not made us safer.
Conclusion
The federal regulations are very clear that the name of the entity on whom the NERC penalty is imposed must be disclosed, along with the settlement agreements and all documents necessary for public scrutiny of the regulatory transaction. FERC has failed to enforce its own regulations, with great harm to the public interest.
For all of the forgoing reasons, I request that the Commission fully review the Notice of Penalty in this docket and require that the identity of “the Companies”, names of the regional entities, the full text of the settlement agreement, and all other redacted information is promptly disclosed to the public.
If FERC’s practice of allowing NERC to hide the names of cybersecurity violators was going to help electric grid security, it should have worked over the past nine years. The Director of National Intelligence says that America’s electric grid is at grave risk of cyberattack—it is obvious that reform of this weak enforcement regime is long overdue.
Respectfully submitted by:
Michael Mabee
[1] This NOP is a departure from past NOPs where the violators were referred to a “Unidentified Registered Entities.” In this NOP, the unidentified entities are referred to as “the Companies.”
[2] Sobczak, Blake and Behr, Peter. “Duke agreed to pay record fine for lax security — sources” E&E News, February 1, 2019. https://www.eenews.net/energywire/2019/02/01/stories/1060119265?fbclid (accessed February 5, 2019).
[3] In fact, there have been several press articles already on this NOP, most identifying Duke Energy as “the Companies.”
[4] See: https://www.nerc.com/pa/RAPA/PA/Performance%20Analysis%20DL/NERC_2018_SOR_06202018_Final.pdf (accessed February 20, 2019).
[5] 18 CFR § 39.7 (b)(4)
[6] NOP, pg. 55.
[7] NOP pg. 55.
[8] It is noteworthy that on February 14, 2019 in a hearing before the Senate Committee on Energy and Natural Resources – a hearing attended by both the President and CEO of NERC as well as the Chairman of the Commission – Senator Angus King noted unequivocally that “the Russians are already in the grid.” See: https://securethegrid.com/senate-cybersecurity-hearing/ (accessed February 20, 2019).
[9] 18 CFR § 388.113, et seq.
[10] FERC Order No. 833 at pg. 17. Also see 18 C.F.R. §388.113(c)(1)(iv).
[11] NOP pg. 56
[12] Coats, Daniel R. “Worldwide Threat Assessment of the U.S. Intelligence Community” Senate Select Committee on Intelligence. January 29, 2019. https://www.dni.gov/files/ODNI/documents/2019-ATA-SFR—SSCI.pdf (accessed February 5, 2019).
[13] See: https://www.nerc.com/pa/comp/Pages/Registration.aspx (accessed February 10, 2019).
[14] We found there were 172 instances of the word “burden” in industry comments on FERC Docket RM17-13-000 (cyber security rulemaking) https://securethegrid.com/grid-cybersecurity-comments-ferc/ (accessed February 10, 2019).


