Duke Redux – A Repeat Cybersecurity Violator Exposed!

Duke Energy was cited twice for the same cybersecurity violations
On September 3, 2019 I received further results of Freedom of Information Act (FOIA) requests I have filed with the Federal Energy Regulatory Commission. One of the documents I received, identifies Duke Energy as the violator in FERC Docket No. NP10-138-000. So, we now know that on July 6, 2010, Duke was fined $5,000 for violating Critical Infrastructure Protection (CIP) standards. We recently learned that Duke Energy was fined $10 million on January 25, 2019 (Duke was outed by the press as the violator).
A comparison of these two Notices of Penalty show that Duke Energy was cited and fined on July 6, 2010 for the same regulatory violations that they were subsequently fined for on January 25, 2019.
Duke Energy gets the dubious honor of being the first company exposed as a repeat violator of the same Critical Infrastructure Protection (CIP) standard.
The Critical Infrastructure Protection (CIP) standards are enforced by the North American Electric Reliability Corporation (NERC) and the regulatory actions or “Notices of Penalty” are submitted to the Federal Energy Regulatory Commission (FERC) for approval. (The public is not given the names of the violators, which under the present system are withheld permanently.)
So, the public was never supposed to know whether or not there are repeat violators. The secret CIP regulatory system has shielded the electric utility industry from such scrutiny for over 9 years. However, there is now a move by FERC and NERC to increase transparency, but I digress. (If you want to read more about this—and what you can do to help—read this report.)
At issue is the requirement that when an employee or contractor is terminated, their access to “Critical Cyber Assets” must be revoked.
In 2010, Duke was cited for this:
“The Registered Entity did not revoke physical access rights to Critical Cyber Assets within seven days for personnel who no longer required access. The Registered Entity discovered seven instances where records could not be located to demonstrate badge deactivations occurred in a timely manner for personnel who no longer required access to Critical Cyber Assets. Subsequently, the Registered Entity submitted a letter in which it identified two additional instances in which revocation was similarly delayed and occurred in the same time frame as the original seven. Therefore, the Registered Entity self-reported a total of nine instances where access badges were not deactivated in a timely manner, following termination of those employees.” [NP10-138-000 NOP, page 2.]
Then in 2019, Duke was cited for this:
“The REs [Regional Entities] determined that the Companies failed to timely revoke a former employee’s electronic access rights, in five instances. In the first instance, the Companies terminated the employee, but the Companies’ manager did not notify the help desk per internal processes so that the help desk could immediately revoke access. In the second instance, the Companies’ contractor’s employment ended, but the account manager did not follow the Companies’ internal process of notifying the appropriate personnel to revoke the contractor’s physical badge access to CCAs within seven calendar days from the date of termination. In the third instance, the Companies required a contractor to go on a 30-day absence, but the contractor’s manager failed to follow the Companies’ internal process of completing the required change access request documentation to revoke the contractor’s physical badge access. In the fourth instance, the Companies failed to revoke access within seven calendar days for an employee who no longer required access to CCAs. In the fifth instance, the Companies failed to remove access for an employee because the badge access system was not designed to process NERC and non-NERC access requests or revocations on the same ticket.” [NP19-4-000 NOP, pages 17-18.]
And this:
“The REs determined that the Companies failed to revoke employees’ access within seven calendar days after access was no longer required, in three instances. In the first instance, the Companies’ manager initiated an access revocation, which was not finalized because the manager inadvertently kept the request in draft form. In the second instance, the Companies did not timely revoke employees’ access rights that were no longer needed. In the third instance, the Companies failed to timely revoke two employees’ authorized unescorted physical access to CCAs.” [NP19-4-000 NOP, page 18.]
And this:
“The REs determined that the Companies did not revoke a contractor’s physical access rights within seven calendar days from the date of termination. [NP19-4-000 NOP, page 18.]
And this:
“The REs determined that the Companies did not timely revoke eight individuals’ unescorted physical access to a [redacted] Physical Security Perimeter (PSP) within 24 hours from termination.” [NP19-4-000 NOP, page 20.]
Granted, Duke is a big company. There is no indication that the 2010 and the 2019 violations were in the same place. But that doesn’t matter. Duke did not get its cybersecurity act together and got penalized $10 million—including some repeat violations.
This information about repeat violations is of interest to the public, investors, Congress and other regulators. Such information should not be withheld. We need to know if we have repeat Critical Infrastructure Protection (CIP) violators and if we have potential bad actors. (I’m talking about bad actors in charge of protecting our critical infrastructures—not the ones attacking them.)
In the weeds with the Duke violations
For those who want more details on the requirements and the two penalty cases, details are below. First, here are the relevant CIP standards and effective dates:
- CIP-004-1 Cyber Security — Personnel & Training (Effective Date: 6/1/2006)
- CIP–004–3a Cyber Security — Personnel & Training (Effective Date: 12/12/2012)
- CIP-004-6 Cyber Security — Personnel & Training (Effective Date: 7/1/2016)
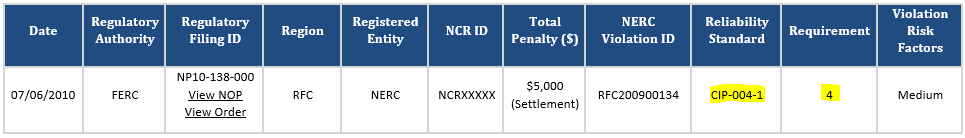
On 7/6/2010 Duke was cited $5,000 (Docket No. NP10-138-000) for:
- CIP-004-1 Requirement 4.2:
- R4.2. The Responsible Entity shall revoke such access to Critical Cyber Assets within 24 hours for personnel terminated for cause and within seven calendar days for personnel who no longer require such access to Critical Cyber Assets.
From NERC’s website on Docket No. NP10-138
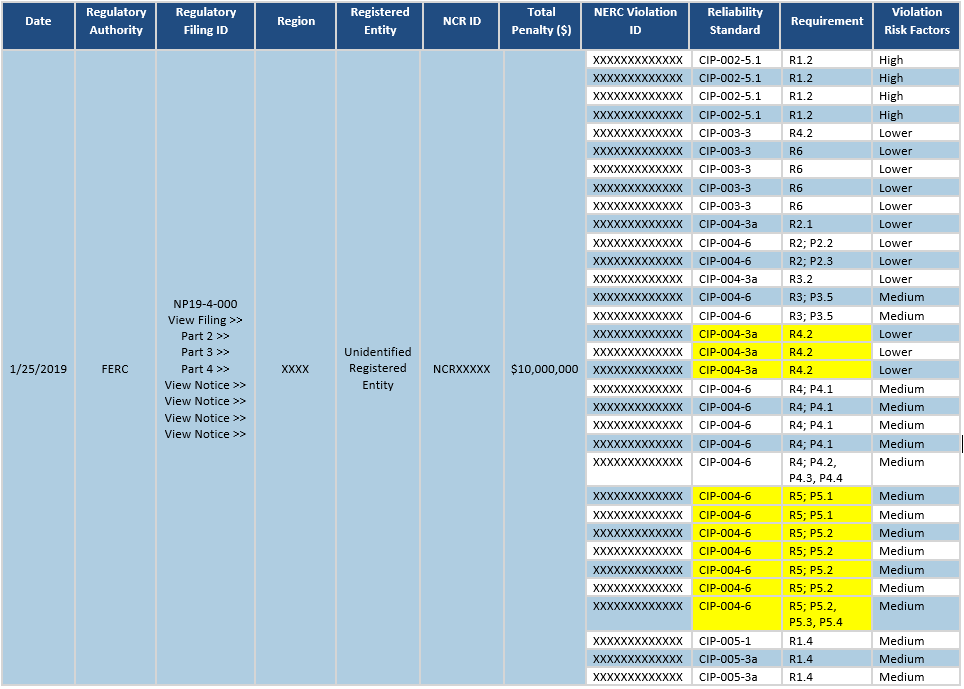
On 1/25/2019 Duke was cited $10,000,000 (in Docket No. NP19-4-000) for numerous violations including:
- CIP–004–3a Requirement R4.2:
- R4.2. The Responsible Entity shall revoke such access to Critical Cyber Assets within 24 hours for personnel terminated for cause and within seven calendar days for personnel who no longer require such access to Critical Cyber Assets.
- CIP-004-6 Table R5 Requirement:
- 5.1 A process to initiate removal of an individual’s ability for unescorted physical access and Interactive Remote Access upon a termination action, and complete the removals within 24 hours of the termination action (Removal of the ability for access may be different than deletion, disabling, revocation, or removal of all access rights).
- 5.2 For reassignments or transfers, revoke the individual’s authorized electronic access to individual accounts and authorized unescorted physical access that the Responsible Entity determines are not necessary by the end of the next calendar day following the date that the Responsible Entity determines that the individual no longer requires retention of that access.
- 5.3 For termination actions, revoke the individual’s access to the designated storage locations for BES Cyber System Information, whether physical or electronic (unless already revoked according to Requirement R5.1), by the end of the next calendar day following the effective date of the termination action.
- 5.4 For termination actions, revoke the individual’s non-shared user accounts (unless already revoked according to Parts 5.1 or 5.3) within 30 calendar days of the effective date of the termination action.
From NERC’s website on Docket No. NP19-4-000
Conclusion
Out of the 255 dockets that I have FOIAs filed for, FERC has so far released 9 names to me. Of those 9 names, two NOPs were for Pacific Gas and Electric (PG&E) for different violations and two NOPs were for Duke Energy (including some repeat violations).
Getting some industry accountability is long overdue. Stay tuned for more in the coming weeks – subscribe to my blog HERE to make sure you don’t miss anything!
###![]()
Click HERE for details on my FOIA requests
