Critical Electric Infrastructure – The Government Must Step Up
Introduction
I am a private citizen who, for over a decade, has conducted public interest research on the security of the electric grid because I recognize the absolutely vital role of this infrastructure in powering every one of the nation’s 16 critical infrastructures and in undergirding not just the well-being but the very survival of our country. I am a retired U.S. Army Command Sergeant Major, and I maintain one of the world’s most comprehensive grid security databases as an unpaid volunteer grid security researcher.[1] I have been quoted by the Wall Street Journal, the Washington Post and many other publications on grid security and have intervened and submitted testimony in over 200 federal dockets on electric grid security issues.
The Department of Energy needs to keep in mind that everybody filing in this RFI has an agenda. My agenda is that I took an oath to “support and defend the Constitution of the United States against all enemies, foreign and domestic.” This is the same oath taken by every uniformed and civilian employee of the United States government, including those at the Department of Energy.
The electric utility industry also has an agenda which is not necessarily the same agenda as the United States government.
The Department of Energy’s Responsibility to Secure the Critical Electric Infrastructure
The preamble of the U.S. Constitution gives the federal government the responsibility to “provide for the common defense.” On February 12, 2013, President Barack Obama implemented Presidential Policy Directive 21 (PPD-21)[2] – Critical Infrastructure Security and Resilience. PPD-21 identifies the 16 critical infrastructures in the U.S. and mandates that:
The Federal Government shall work with critical infrastructure owners and operators and SLTT [state, local, tribal, and territorial] entities to take proactive steps to manage risk and strengthen the security and resilience of the Nation’s critical infrastructure, considering all hazards that could have a debilitating impact on national security, economic stability, public health and safety, or any combination thereof.
PPD-21 identifies the energy sector as uniquely critical due to the enabling functions it provides across all 16 critical infrastructure sectors. The electric grid is the lynchpin: All 16 critical infrastructures, including the rest of the energy sector and our national security apparatus, depends on the electric grid. Therefore, any threat to the electric grid is a threat to U.S. national security. The Department of Energy is designated as the Sector Risk Management Agency for the energy sector.[3]
The North American electric grid is an amazing human accomplishment. It is the largest machine in the history of the world, built piece by piece over many generations. This machine is literally the life support system for the United States.
The entire electric grid must be secured – not just part of it. The “electric grid” is actually thousands of entities, both public and private sector, that operate in an interconnected system to facilitate the generation, transmission and distribution of electrical power. The grid is made up of power generation—such as nuclear, coal and gas-fired power plants, hydroelectric facilities, wind turbines and solar farms, high voltage transmission lines that span long distances across the country and local distribution lines which bring the power to our homes and businesses.
This interconnected—and vulnerable—patchwork is what allows the United States to support her human population. Everything that enables 330 million people in the country to survive is wholly reliant on the electric grid. All of our critical infrastructures, including food, water, fuel, transportation, financial, communications, medical systems and our national defense infrastructure, are all completely dependent on the electric grid. This cannot be overemphasized: Our national security is dependent on the electric grid.
As we know from the recent Colonial Pipeline and SolarWinds cyberattacks, the energy sector is targeted by state adversaries and criminals. And as we know from the Texas grid collapse in February of 2021, even extreme weather threatens the grid. We have known about the many vulnerabilities and threats to the critical electric infrastructure and the energy sector for decades.
There are four major challenges to securing the critical electric infrastructure. I will briefly outline each below and provide recommendations. The U.S. Department of Energy must provide extraordinary leadership in order for the U.S. to overcome these challenges.
A dysfunctional regulatory bureaucracy continues to buy the electric industry’s bill of goods.
- The first challenge is the mind-numbingly complex regulatory structure of the electric grid.
There are few mandatory standards in place for the protection of the critical electric infrastructure. The few that do exist do not apply to the entire electric grid, just small portions of it. And these few existing standards are insufficient. On the issue of security, some of the grid is self-regulated. Other parts have no mandatory security requirements whatsoever. The federal government under current law does not have clear authority to mandate that the electric grid adopt measures to protect itself from threats.
The North American Electric Reliability Corporation (NERC) is a not-for-profit corporation that acts as the self-regulatory organization “whose mission is to assure the reliability of the bulk power system (BPS) in North America.” The Federal Energy Regulatory Commission (FERC) is an independent federal agency that regulates the interstate transmission of electricity, natural gas, and oil. FERC’s specific authority over the electric grid is to “oversee the reliability of the bulk power system.” The few mandatory reliability standards and “Critical Infrastructure Protection” (CIP) standards that do exist are written by the electric utility industry and, due to the myriad of exemptions written into the standards, apply only to certain parts of the bulk power system.
The bulk power system consists of approximately 1,500 entities operating at 100 kilovolts or higher which are regulated by NERC, overseen by FERC. However, the bulk power system does not include power generation or distribution to end-users. Generation and distribution are under the jurisdiction of state public utility commissions (PUCs). This means that there are over 60 state and federal government agencies as well as a number of non-profit corporations involved in the regulation of the electric grid. Unbelievably, there is literally no government authority over the security of the electric grid unless an individual state enacts a mandate on its own. Most have no such state mandates.
The Kleinman Center for Energy Policy charitably said: “Today’s electric grid is developing within the confines of a century-old regulatory system.”[4] Put more bluntly, the regulatory regime, built over generations like the grid itself, most closely resembles a Rube Goldberg cartoon. From a security standpoint, it is cumbersome, slow, bureaucratic and inefficient. Our decades-long inability to secure the critical electric infrastructure through the existing regulatory regime will continue to put the country in danger.
Since protection of the critical electric infrastructure is imperative for national security, we simply cannot use the current regulatory morass to get the job done. The United States must mandate the protection of the critical electric infrastructure – whether public or private sector. We do not have years or decades to allow protection to soak in or move through osmosis. Protecting the critical electric infrastructure requires immediate and mandatory actions – and accountability for violators.
We have known for decades that the critical electric infrastructure is vulnerable to threats, yet little has been done. For example, in 1981 – over 40 years ago – the General Accounting Office (now the Government Accountability Office, or GAO) issued a report titled: “Federal Electrical Emergency Preparedness Is Inadequate.”[5] GAO noted:
If saboteurs, terrorists, or an enemy attacked the Nation’s electric power system, would the Federal Government be prepared to handle the resulting energy disruptions?
Probably not, because the Department of Energy has failed to prepare required electric emergency preparedness plans. A national plan to cope with the problems caused by a loss of electricity–which would virtually halt communication, transportation, and distribution systems–is essential, because utilities and the States cannot be expected to deal with such emergencies on their own.
The 1981 report further noted:
The consequences of such a power outage are staggering. Electric power is essential to maintaining the Nation’s military readiness. Without adequate or reliable power, most industrial activity would be disrupted. Power outages can disrupt the operation of computers, commercial business, water and sewage treatment plants, mass transit and traffic control systems, as well as many other aspects of life.
In the United States, electric power is generated by some 3,500 utility companies, sent over thousands of miles of high voltage transmission lines, and distributed over low voltage feeder lines to end users. The system is a highly complex, interconnected industry network covering the United States and parts of Canada.
Electric power systems are highly dependable, but are very vulnerable to disruptions from acts of war, sabotage, or terrorism. In the region GAO looked at:
- An attack on just eight substations could disrupt power to the entire region for a long time. (See p. 8.)
- Damage to just four substations could disrupt power to one city for up to a year. (See p. 8.)
- Damage to just one substation could leave a key military facility without power. (See p. 8.)
What is most shocking about this 1981 GAO report is that in 2021 there is still no physical security requirement for most of the critical electric infrastructure. The one NERC standard that exists, CIP-14-2, exempts generation facilities, does not apply to distribution and applies to very few facilities in the bulk power system. Moreover, there have been 721 physical attacks against the critical electric infrastructure since 2010.[6] In sum, in 2021 there are still no meaningful physical security requirements for the electric grid.[7]
Since the industry and the regulators haven’t addressed the physical security of our critical electric infrastructure in four decades, extraordinary leadership is needed now to get the job done.
Another example is the lack of supply chain cybersecurity requirements. With the recent SolarWinds and Colonial Pipeline cyberattacks, there is no need to belabor the threats posed by cyberattacks to the energy sector. However, between 2006 and 2019, according to data from the U.S. International Trade Commission, the U.S. imported 300 “Liquid dielectric transformers having a power handling capacity exceeding 10,000 kVA” from China.[8]
At least 200 of these Chinese large power transformers found their way into our electric grid.[9] Others may have been bought by large industries, but it is certain that most of these 300 Chinese large power transformers have embedded themselves in our critical infrastructures in the U.S. There is no requirement that anybody check these hundreds of transformers that have already been installed. There is no supply chain cybersecurity requirement on the thousands of companies that may buy components for the critical electric infrastructure from China.[10]
To summarize the problem: We are buying critical equipment from China to install into our critical electric infrastructure that China is already hacking.
What could possibly go wrong?
The present regulatory scheme relies on thousands of companies who own, operate or supply the critical electric infrastructure to voluntarily do the right thing. There is no requirement that they do so. This brings us to the second major challenge.
-
The second challenge is the electric utility industry itself.
The electric utility industry has an agenda which is not necessarily the same agenda as the United States government. In fact, according to The Center for Responsive Politics, the electric utilities in the 2020 cycle:
- Spent $108,468,019 on lobbying the U.S. Congress.[11]
- Made total contributions to the U.S. Congress of $28,562,003.[12]
- Made $11,626,034 in political contributions to members of the U.S House.
- Made $5,140,906 in political contributions to members of the U.S. Senate.
- Total lobbying and contributions in the 2020 cycle: over $137 million.
In the last decade the electric utility industry has spent $1.2 billion lobbying the U.S. Congress and another $150 million in “contributions.” (Not including lobbying and contributions at the state level.) Imagine if this $1.2 billion, which largely originated from the bills of ratepayers, was put towards electric grid security rather than lobbying against further regulation.
The industry’s lobbyists have embedded themselves over the years, as “partners” in DOE and FERC via the Electric Subsector Coordinating Council (“ESCC”) and trade organizations such as the Edison Electric Institute (“EEI”), the American Public Power Association (“APPA”), the National Rural Electric Cooperative Association (“NRECA”), the Large Public Power Council (“LPPC”), the Transmission Access Policy Study Group (“TAPS”), the Electric Power Supply Association (“EPSA”), WIRES, and the Electricity Consumers Resource Council (“ELCON”). These industry groups have actively fought against grid security regulation, mandatory critical infrastructure protection standards and public transparency.
The industry does not represent the public interest. They do not represent the U.S. government.
Here are a few facts about the electric industry’s posture on grid security:
- After the Great Northeast Blackout of 2003, the industry was forced to write a mandatory vegetation management standard. (Yes, the industry writes its own standards.) The standard took a decade to finally be implemented in 2013.[13] Problem solved? Ask the people of Paradise, California where 85 people died in the 2018 Camp Fire and PG&E subsequently plead guilty to 85 felony counts for its role in that catastrophe.[14]
- After the spectacular physical attack against a transformer in Metcalf, California in 2013[15] the industry advised against a mandatory physical security standard.[16] They were forced to write the standard. The resulting weak physical security standard that exempts most facilities from compliance. (Generation facilities are specifically exempted.) As a result, there have been hundreds of physical attacks against the grid since the “physical security standard” was implemented.[17]
- Despite the well-documented physical security problem in the critical electric infrastructure[18], the industry continues for fight against stronger physical security regulations. The inadequacy of the physical security standards was highlighted in a complaint filed with the Federal Energy Regulatory Commission (FERC) on January 29, 2020 alleging that grid physical security was inadequate.[19] At the urging of the industry, on June 9, 2020 FERC dismissed the complaint.[20]
- The industry vehemently fought FERC’s Notice of Proposed Rulemaking to establish a mandatory standard for Geomagnetic Disturbances.[21] Once forced to write a standard (TPL-007-1) the effectiveness of this industry-written standard is still the subject of considerable debate.[22]
- The industry has consistently fought against stronger supply chain cybersecurity standards. The inadequacies of the cybersecurity standards were highlighted in a complaint filed with the Federal Energy Regulatory Commission (FERC) on May 11, 2020 about the need for increased supply chain cybersecurity.[23] At the urging of the industry, on October 2, 2020 FERC dismissed the complaint.[24] A month and a half later, the SolarWinds hack came to light and the regulators – NERC and FERC – were caught flat-footed.
- The irony of the SolarWinds hack is that since 2017, the industry vehemently fought against modifying CIP standards to require detection, mitigation and removal of malware from the electric grid.[25] While fighting this common-sense petition for rulemaking, the head of NERC testified in 2019 that he didn’t know whether there was Russian or Chinese equipment or software already installed in the grid.[26] SolarWinds was first detected in 2020 but to this day, thanks to the industry’s diligent efforts, there is no requirement that malware be detected, mitigated or removed.
- The Texas grid collapse in February of 2021, which was responsible for over 150 deaths[27] and between $80 billion–$130 billion in economic loss[28], was a repeat offense. Similar outages for identical reasons occurred in 1989 and 2011. The government and the industry have failed to fix the underlying critical electric infrastructure issues that caused all three incidents. Yet the industry urged FERC to take no action to investigate whether the existing standards were followed or if improvements are needed.[29] At the urging of the industry, FERC dismissed a complaint on this issue on May 26, 2021.[30]
- There is currently no mandatory standard for protecting the grid against an electromagnetic pulse (EMP) attack – a standard that the industry opposes and FERC declines to order. The industry enlisted its Electric Power Research Institute (EPRI) to “study” the electromagnetic pulse (EMP) threat to the electric grid. EPRI disregarded the findings of the Congressional EMP Commission[31] and severely understated the EMP threat. The resulting disingenuous report by EPRI (which was lauded by the industry) has placed the United States in great danger.[32] EPRI’s report is contradicted by multiple experts of the Electromagnetic Defense Task Force (EDTF) [33] and by a January 11, 2021 Department of Energy memo.[34] However, the industry continues to propound that the EPRI report is the benchmark report for EMP protection of the critical electric infrastructures. Regardless, there is no movement towards developing an EMP standard to protect the electric grid.
- Edison Electric Institute (EEI) is the trade organization that purports to represent “all U.S. investor-owned electric companies.” EEI is a frequent intervenor and commenter in FERC dockets and Congressional hearings related to Critical Infrastructure Protection (CIP) standards and issues. EEI spends millions of dollars annually lobbying the U.S. Congress on matters pertaining to the U.S. critical electric infrastructure. EEI also makes contributions to key members of Congress involved in critical infrastructure security legislation and oversight. EEI counts among its members State Grid Corporation of China, which is a state-owned corporation, owned by the government of the People’s Republic of China. EEI also counts as a member Power Assets Holdings, a company based in Hong Kong (which China calls “Hong Kong Special Administrative Region of the People’s Republic of China”).[35]
The U.S. Government has been concerned about the cybersecurity of the critical electric infrastructure since at least 2003,[36] the security of the electric grid from physical threats since at least 1981[37] and electromagnetic pulse (EMP) threats since at least 1975.[38] In other words, we have been talking about securing our critical electric infrastructure for over four decades from the very threats we still face today.
The electric utility industry has lobbied and fought against grid protection regulations every step of the way. After the Great Northeast Blackout of 2003, Congress passed the Energy Policy Act of 2005 which added Section 215 to the Federal Power Act. However, this moved the needle very little on the security of the critical electric infrastructure. The impact was we moved from “voluntary” self-regulation to “mandatory” self-regulation – but only for a small portion of the whole critical electric infrastructure. Perhaps the problem we face today was best summarized in 2003 in Congressional testimony when the bill was being debated:
“We must not rely on industry self-regulation. The proposal to move from voluntary self-regulation to mandatory self-regulation misses the point. The difficulty is not the voluntary versus the mandatory. It is the ‘self’ part. We need clear accountability to public authorities.”[39]
While public-private partnerships have their place, the industry has lobbied, promoted and ultimately hornswoggled the federal government into a system of “all carrots and no stick.” They laud the public-private partnerships and have fought for decades against regulation and mandatory standards to secure the critical electric infrastructure. Everything they do is calculated to kick the grid security can down the road and commission more “studies.” When finally forced to write a mandatory standard, the resulting weak standards should not be surprising. This hands-off approach has not worked and today our national security is jeopardized.
In short, the electric utility industry has had their chance – and for many more years than this regulatory boondoggle should have been allowed to go on. Enough is enough. The present dismal state of our critical electric infrastructure security is because the federal government listened to the electric utility industry and applied a light regulatory touch at the urging of industry lobbyists.
The electric utility industry’s agenda is not and cannot be the Department of Energy’s agenda. The tail has been wagging the regulatory dog for decades on grid security – which is the primary reason we are in a national security crisis today.
Unfortunately, the United States has occasionally been a bad judge of character. A rogues’ gallery including Osama bin Laden, Saddam Hussein and Manuel Noriega count themselves as former U.S. allies. Here, we have placed our trust and our national security in the hands of an industry with a checkered past[40]: Samuel Insull, Enron, PG&E’s multiple felony convictions, the recent Ohio and Illinois bribery scandals to name only a few. In fact, R Street Institute pointed out[41]:
“Policymakers should not dismiss these developments as merely the work of a few bad actors, but as the latest evidence of an established behavioral pattern tied to perverse incentives from flawed institutions.”
We should not trust the electric utility industry. If after all the industry’s efforts and counsel over the past decades, our critical electric infrastructure is not secure, perhaps their agenda is not the same as that of the United States government.
When some of the thousands of entities who own, operate or supply the electric grid do the right things, we should incentivize them. But we must hold those who endanger the critical electric infrastructure accountable. And we must ensure that the public, Congress and state regulatory authorities have the transparency necessary to scrutinize the results.
The Department of Energy must show extraordinary leadership in the face of powerful and influential special interests in order to secure the critical electric infrastructure.
Public, Congressional and state scrutiny is needed.
The failure of the industry and the government for decades to secure the critical electric infrastructure from the known threats is punctuated by, at best, confusing and conflicting information provided to the public as well as the downright coverup of misconduct. We need a policy of adequate public information, transparency and accountability.
-
The third challenge is that OE-417 data is inadequate, inaccurate, not updated and conflicts with data from other official sources.
Utility companies and grid operators are required to submit reports on electric disturbance events to the Department of Energy (DOE) on a Form OE-417 (“Electric Emergency Incident and Disturbance Report”).
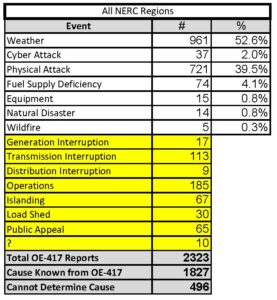
I did an analysis of all the publicly available OE-417 data from 2010 through 2020.[42] First of all, there were 166 different “event types” reported many of which were either duplicates or related. For example, there were at least 24 different “event types” that denoted a physical attack. There were at least 50 “event types” that denoted a disturbance caused by weather. I grouped these 166 “event types” into 15 categories (actually “causes”) so that we could get a sense of what has actually threatened the electric grid in the past decade.
There has been a total of 2,323 electric disturbance events filed during the period of January 1, 2010 through December 31, 2020.
Unfortunately, the public OE-417 data is so bad that there were 496 electric disturbance events where I was unable to identify a cause (21% of the reports). These are highlighted in yellow in the chart. I was able to identify a cause in 1,827 electric disturbance events, or 79% of the OE-417 reports filed. (I used this known population of 1,827 for the percentages in the above chart and the study below.)
The results are disturbing to say the least.
Weather: As one might suspect, weather was the cause of the majority of the disturbances, 961 events, or 53%. If one believes that weather is getting worse in recent years, then this number should be of great concern.
Physical Attacks: Shockingly, there were 721 physical attacks on the grid, or 40% of the incidents. As previously mentioned, the “physical security standards” for our electric grid are weak in the few areas of the bulk power system where they do apply, but there are no mandatory physical security standards for most of the electric grid.
Fuel Supply Deficiency: There were 74 events, or 4% of the events. related to fuel supply deficiency. The Colonial Pipeline cyberattack raises great concerns for the security of fuel supply to generation plants.
Cyber Attacks: I was also surprised to learn that there have been 37 cyberattacks reported during this period (2% of the reports). What is most disturbing is that during the same period, the North American Electric Reliability Corporation (NERC) annual reliability reports and other government agencies seem to paint completely different pictures.
The data given to the public in the OE-417s is dramatically different than what NERC portrays to the public in their self-serving annual “State of Reliability Reports.” [43] Here is what NERC reported during this same period:[44]
- 2020 Report (page x) “There were no reportable cyber or physical security incidents in 2019.” (Note: There was a significant and widely reported cyberattack in the grid in 2019 – which does appear in the OE-417 and was widely reported in the press[45] but disingenuously omitted from NERC’s public report.)
- 2019 Report (page ix): “In 2018, there were no reported cyber or physical security incidents that resulted in an unauthorized control action or loss of load.”
- 2018 Report (page viii): “In 2017, there were no reported cyber or physical security incidents that resulted in a loss of load.”
- 2017 Report (page 3): “In 2016, there were no reported cyber or physical security incidents that resulted in a loss of load.”
- 2016 Report (page v): “In 2015, there were no reported cybersecurity incidents that resulted in loss of load. There was one physical security incident that resulted in a loss of approximately 20 MW of load.”
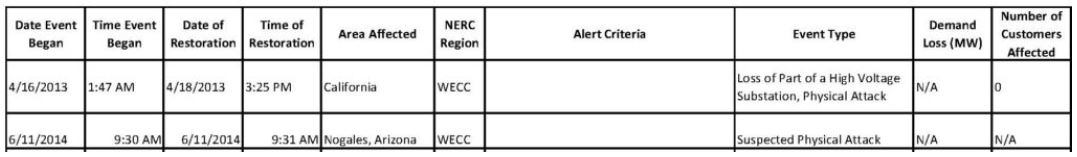
- 2015 Report (page 7): “[N]o Reportable Cyber Security Incidents or physical security reportable events resulted in loss of load on the BPS in 2014.” (Note: Misleading, since the Nogales Station in Arizona was attacked by an IED in 2014. [46])
- 2014 Report: No mention of cyber or physical attacks. (Note: Misleading, since the Metcalf Transformer attack took place in 2013.[47])
- 2013 Report: No mention of cyber or physical attacks.
- 2012 Report: No mention of cyber or physical attacks.
- 2011 Report: No mention of cyber or physical attacks.
There is clearly a huge disconnect between what the industry defines as a cybersecurity or physical security incident and what is reported on the OE-417s. The below chart reproduces the public OE-417 entries for the Metcalf physical attack (2013) and the Nogales physical attack (2014):
While this minimal information was reported on the OE-417, NERC did not find Metcalf or Nogales noteworthy enough for their annual reports. These events were significant physical attacks against the grid and NERC chose not to disclose them to the public.
The discrepancies in physical security and cybersecurity reporting can be summarized as follows:
- There were 721 physical attacks against the grid reported on the OE-417’s between January 1, 2010 through December 31, 2020, yet according the NERC there was only one during the same period.
- There were 37 cyberattacks against the grid reported on the OE-417’s between January 1, 2010 through December 31, 2020, yet according the NERC there were none during the same period.
Meanwhile, federal government reports on cyberattacks against the energy sector during the same periods paint a completely different picture. For example, here’s what the United States Government Accountability Office (GAO) had to say in Congressional testimony on October 21, 2015 on cyberattacks[48]:
“Cyber incidents continue to affect the electric industry. For example, the Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team noted that the number of reported cyber incidents affecting control systems of companies in the electricity subsector increased from 3 in 2009 to 25 in 2011. The response team reported that the energy sector, which includes the electricity subsector, led all others in fiscal year 2014 with 79 reported incidents. Reported incidents affecting the electricity subsector have had a variety of impacts, including hacks into smart meters to steal power, failure in control systems devices requiring power plants to be shut down, and malicious software disabling safety monitoring systems.”
And the U.S. Department of Homeland Security reported 59 cyberattacks on the energy sector in FY 2016[49] and 46 cyberattacks in FY 2015.[50] Both the GAO and DHS data conflicts with the OE-417 data which shows only 37 cyberattacks from 2010 through 2020.
Astoundingly, NERC reported to the public that there were no cybersecurity incidents in their annual reliability reports for the same periods.
NERC’s definitions apparently don’t consider most cyberattacks to be “reportable cyberattacks.” The public is confused when the U.S. government reports a substantial number of cyberattacks against the energy subsector and NERC reports no cyberattacks.
While the industry may argue that there are different populations of regulated entities covered by the various reports, clearly, more transparency is needed for the public, investors, Congress and other regulators to understand these discrepancies and make sense of this conflicting information. Regulatory complexity requires even better public information.
Moreover, the requirement that the information be updated is obviously not being followed by the industry, or enforced by DOE, making the information of substantially less value.
For example, attached as Exhibit D is the public OE-417 data for the TRE Region (i.e., ERCOT) for February 2021 – the period covering the Texas grid collapse. One of the OE-417 requirements is that the information is supposed to be updated. Clearly, the information has not been updated. By now we should know the “Demand Loss (MW)” for each entry and the “Number of Customers Affected” but many entries still say “Unknown.”
This is not unique to this incident. Attached as Exhibit E is the public OE-417 data (then called the EIA-417) for the Great Northeast Blackout of 2003 in which 45 million people in the U.S. lost power, as well as another 10 million in Canada, the EIA-417 data in 2021 shows “Number of Customers Affected” were 7,369,487. Also, to this day, the “Type of Disturbance” is listed as “Unknown.”
The confusing and inaccurate public information needs substantial improvement. If the public data is any indication, then the Department’s internal data on electric disturbance events may also be lacking, making analysis of issues in the critical electric infrastructures problematic.
The Department of Energy must improve the quality of the OE-417 data so causes of disturbance events can be meaningfully determined and electric disturbance events analyzed. DOE needs to enforce the reporting requirements to ensure the information is accurate. Substantial penalties should apply where entities fail to report or update required information.
-
The fourth challenge is the coverup of the names of regulatory violators, which prevents public, Congressional and state scrutiny and shields violators from accountability.
Since July of 2010, the identities of every violator of NERC’s Critical Infrastructure Protection (CIP) standards have been withheld from the public, investors, state Public Utility Commissions (PUCs) and Congress. The electric utility industry, through its regulatory mouthpiece NERC – aided and abetted by FERC – are attempting to permanently withhold the names of the violators despite the fact that the violations in almost all cases have been long ago mitigated.
Between July of 2010 and April of 2021 there have been 275 FERC dockets involving over 1,500 “Unidentified Registered Entities” – the industry euphemism for violators whose names are being withheld from the public. In every single case, the identity of the regulatory violator was withheld from the public, Congress and state regulators. This issue is the subject of multiple Freedom of Information Act (FOIA) Requests and a lawsuit against the Federal Energy Regulatory Commission under FOIA.[51] The electric utility industry vehemently opposes the release of the names of violators.
We know for a fact from open sources that the Russians and the Chinese have been in our electric grid for over a decade:
- April 8, 2009 Wall Street Journal: “Electricity Grid in U.S. Penetrated By Spies.” [52]
- January 10, 2019 Wall Street Journal: “America’s Electric Grid Has a Vulnerable Back Door—and Russia Walked Through It.” [53]
- January 29, 2021 Wall Street Journal: “Suspected Russian Hack Extends Far Beyond SolarWinds Software, Investigators Say.”[54]
So, if keeping the names of the CIP violators from the public was going to make us safer, wouldn’t it have worked by now? A fair conclusion is that “secret regulation” of CIP standards has not worked. It appears from the available evidence that the real reason for the “protection” of the names of the regulatory violators is because the industry does not want to be held accountable for doing more than the minimum on physical and cyber security. There appears to be no legitimate security reason to withhold the names of regulatory violators in perpetuity as is currently the practice.
Notably the electric utility industry has threatened to stop “self-reporting” violations if FERC begins to release the names of CIP violators. The Trade Associations’ Motions to Intervene in FERC Docket No. NP19-4-000[55] contains a not so thinly veiled threat:
“If the Commission begins releasing entity names in addition to the information already made public in the posted Notices of Penalty, then Registered Entities may re-evaluate whether they will continue to self-report security information knowing that providing such information to their regulators may be disclosed to the public, including to people seeking to attack their systems. In addition, Registered Entities also may re-evaluate what information is included in their mitigation plans.”
This is an extraordinary threat that the entities in the industry represented by the Trade Associations, who are subject to NERC’s mandatory reliability standards under federal law,[56] will essentially engage in a regulatory mutiny if the Commission decides to release the names of regulatory violators to the public, as its past orders and regulations require.
The industry is essentially arguing that the names of the regulatory violators constitute “Critical Electric Infrastructure Information” (CEII) and should be withheld from the public permanently (even after the violations are mitigated). This argument is unsupported by FERC regulations and past FERC orders.[57]
There is a public interest in disclosing the names of regulatory violators because:
- Disclosing the names of the violators might lead the public and Congress to assess how well the regulatory system is working.
- This information would inform the public, investors, PUCs and Congress as to whether the current regulatory system can adequately thwart threats to the grid.
- This information could lead the public, investors, PUCs and Congress to conclude that better investment in the critical infrastructures is necessary.
These are public policy questions, not CEII.
Moreover, many companies transcend regulatory lines. Many companies fall under both FERC/NERC and state public utility commission (PUC) jurisdiction and possibly other agencies, such as the Nuclear Regulatory Commission (NRC) and the Securities Exchange Commission (SEC).
- State PUC’s need to know the identities of the CIP violators because, among other things, state PUC’s often control the funding for mitigation.
- Some of these companies may supply critical DOD and DHS facilities. DOD and DHS need to know if companies they are dependent upon to power facilities critical to national security are violating CIP standards.
- Some of these companies may operate nuclear generation plants and fall under the jurisdiction of the NRC as well as FERC/NERC and a PUC (or more than one PUC). These regulators all need to know if the companies they regulate are in violation of CIP standards.
- Some of these companies are also regulated by the Securities Exchange Commission and have reporting requirements for material events. Since the names of CIP violators are being covered up, investors are unaware of the cybersecurity risks that these publicly traded companies face—and whether the “C Suite” is taking appropriate actions to mitigate (or at least disclose) investor risk.
It is hard to imagine how such a Balkanized regulatory system would function in any context, and clearly it is not functioning efficiently in terms of the critical electric infrastructure—one in which the lives of 330 million Americans and our very national security depends.
Until the regulatory system is reformed by Congress, accountability, disclosure and transparency are critical to our national security. There is no possible way for there to be accountability for the thousands of companies involved in the generation, transmission and distribution of electric power in the U.S. except for transparency by DOE, FERC and NERC.
The public, state regulators and investors also have a need to know who violates mandatory CIP standards. Consider the following:
- Who is paying for the CIP violation fines—the ratepayers or the shareholders?
- Who is paying for any mitigation ordered or agreed upon—the ratepayers or the shareholders?
- Most importantly, who decides who pays?
The last question is easy: Absent transparency, the regulatory violator decides who pays. This is why it is critical that FERC release the names of the regulatory violators along with sufficient information so that the public (“ratepayers”), investors (“shareholders”), the PUCs (the ones who should be making these decisions) and Congress (the oversight) can see what is happening.
In 2018, PG&E Corp was fined 2.7 million dollars for a cyber breach (which was exposed by one of my Freedom of Information Act requests).[58] PG&E presumably also had to spend an unknown amount (but likely a substantial amount) of money on mitigation. Somebody had to pay for all of this. Because I could find no disclosure of the event or its costs in PG&E’s filings with the Securities and Exchange Commission, it is impossible for the public to know whether the shareholders or the ratepayers ate these costs—I am sure both groups would like to know.
Does it make a difference in who should pay if a company is a repeat CIP violator? Does it make a difference in who should pay if the company is negligent?
The last one who should be deciding who pays is the regulatory violator. This decision should be made by the appropriate regulator (the PUC) with full transparency to the two possible victims: the ratepayers and the shareholders.
Ratepayers and investors deserve transparency and accountability. PUCs and Congress deserve sufficient information to effectively regulate and govern. Regulatory violators do not deserve reputational protection by the regulators at the expense of the public interest.
In sum, mandatory CIP standards should protect the U.S. electric grid by holding the electric utility companies and grid operators accountable to protect the portion of the critical electric infrastructure that they own or operate. Instead, the electric utility industry has twisted this regulatory scheme into a sham where companies have no incentive to do more than the minimum. If caught violating a CIP standard, NERC and the Regional Entities will settle the matter privately with the “unidentified registered entities” negotiating a “penalty” that the “unidentified registered entities” are willing to pay and will keep the matter from public view. It looks like a system of back-room settlements and handshake penalties. A great deal for the “unidentified registered entities”—not so much for the American people or the security of the critical electric infrastructure.
Conclusions and Recommendations:
The title of this request for information is “Ensuring the Continued Security of the United States Critical Electric Infrastructure.” In order to accomplish this, given the aforementioned four challenges, the U.S. Department of Energy, the Department of Homeland Security and Congress must provide extraordinary leadership. Such federal leadership has been lacking for over four decades.
Recommendations for the U.S. Department of Energy
- The Department of Energy must use to the fullest extent all federal regulatory authority available to mandate and enforce critical electric infrastructure protection and seek additional authority from Congress to do so. We need to address the entire infrastructure: Generation, Transmission and Distribution. This is a matter of national security and cannot be left to “self-regulation” at the discretion of special interests, such as the electric utility industry.
- The Department of Energy must balance industry input and influence with other viewpoints. Public-private partnerships related to the critical electric infrastructure for years have been industry driven and “all carrots and no stick.” This has clearly not worked. Critical electric infrastructure owners, operators and suppliers must be held accountable for protecting the electric grid. Critical electric infrastructure protection must be mandatory – not voluntary. Severe penalties and accountability are necessary for violators. Experts from outside the industry and those representing the public interest must have a voice.
- The Department of Energy must revamp its OE-417 data to make it accurate and useful to the public and other stakeholders. The public should not be getting different and conflicting pictures from DOE, DHS and FERC (through NERC). Reporting on the OE-417 is mandatory. However, DOE needs to enforce the accurate reporting of incidents and disturbances and enforce updates to the information.
- The Department of Energy must hold the electric utility industry accountable for failures to secure the critical electric infrastructure. Such accountability includes public, congressional, state and investors having access to the names of violators of Critical Infrastructure Protection (CIP) standards. DOE and FERC cannot continue to let the electric industry hide its dirty laundry from the public and avoid accountability by continuing to allow a cover-up that has endangered the critical electric infrastructure by allowing violators and the regulatory system to avoid any modicum of accountability.
Recommendation for Congress and the U.S. Department of Homeland Security
With multiple sectors of the U.S. critical infrastructures under current attack[59], immediate and decisive Congressional action is needed:
- Legislation is needed mandating that reasonably prudent cybersecurity measures be taken by all companies, public or private sector, that are part of the 16 critical infrastructure sectors described in Presidential Policy Directive 21.[60]
-
- The Chief Executive Officer of each such critical infrastructure company must be required to certify periodically to DHS that they have reasonably prudent cybersecurity measures in place that have been reviewed and approved by the Chief Executive Officer of the company.[61]
- There must be civil and criminal penalties for false certification or failure to submit such certifications.
- These certifications should be made available to the public as well as state and federal authorities.
- There must be whistleblower protections for employees of the critical infrastructures who report violations of laws, regulations or standards to their employer, regulators or the government.[62]
Respectfully submitted,
Michael Mabee
Fort Worth, TX
Email: [email protected]
Phone: (516) 808-0883
Attachments: Exhibits A-F
CC:
U.S. Senate Committee on Energy and Natural Resources
U.S. House Committee on Energy and Commerce
U.S. Department of Homeland Security – Cybersecurity & Infrastructure Security Agency
Footnotes
[1] Available at: https://securethegrid.com/government-documents-emp-and-grid-security/
[2] Available at: http://bit.ly/2NUr04k
[3] See: https://www.cisa.gov/energy-sector
[4] Peskoe, Ari. Kleinman Center for Energy Policy. “Power Over the Twenty-First Century Electric Grid.” April 10, 2018. https://kleinmanenergy.upenn.edu/research/publications/power-over-the-twenty-first-century-electric-grid/
[5] General Accounting Office (GAO). “Federal Electrical Emergency Preparedness Is Inadequate.” EMD-81-50. May 12, 1981. http://bit.ly/354ZN4i
[6] See OE-417 data and analysis at: https://securethegrid.com/oe-417-database/
[7] Attached as Exhibit A is the complaint on the inadequacy of the electric grid physical security filed with FERC on January 29, 2020 and February 19, 2020. FERC dismissed the complaint on a technicality at the urging of the electric utility industry.
[8] See: https://securethegrid.com/the-u-s-has-300-chinese-large-power-transformers/
[9] E&E News. “China and America’s 400-ton electric albatross.” April 25, 2019. https://www.eenews.net/stories/1060216451/ Also see: Smith, Rebecca. Wall Street Journal “U.S. Seizure of Chinese-Built Transformer Raises Specter of Closer Scrutiny.” May 27, 2020. https://www.wsj.com/articles/u-s-seizure-of-chinese-built-transformer-raises-specter-of-closer-scrutiny-11590598710
[10] Attached as Exhibit B is the complaint on the inadequacy of the electric grid cyber security filed with FERC on May 11, 2020. FERC dismissed the complaint on a technicality at the urging of the electric utility industry.
[11] See: https://www.opensecrets.org/industries/lobbying.php?cycle=2018&ind=E08
[12] See: https://www.opensecrets.org/industries/contrib.php?ind=E08&Bkdn=DemRep&cycle=2020
[13] See: https://www.ferc.gov/industries-data/resources/tree-trimming-and-vegetation-management
[14] San Francisco Chronicle. “PG&E, a ‘killer company,’ admits to 85 felony counts. Now what?” March 29, 2020. https://www.sfchronicle.com/business/article/PG-E-a-killer-company-admits-to-85-felony-15163078.php
[15] Smith, Rebecca. The Wall Street Journal. “Assault on California Power Station Raises Alarm on Potential for Terrorism.” February 5, 2014. https://www.wsj.com/articles/assault-on-california-power-station-raises-alarm-on-potential-for-terrorism-1391570879 and Smith, Rebecca. Wall Street Journal. “U.S. Risks National Blackout From Small-Scale Attack.” March 12, 2014. https://www.wsj.com/articles/SB10001424052702304020104579433670284061220
[16] NERC’s then CEO Gerry Cauley told Congress in a February 12, 2014 letter: “I do not believe it makes sense to move to mandatory standards at this time. There are more than 55,000 substations of 100 Kv or higher across North America, and not all those assets can be 100% protected against all threats. I am concerned that a rule-based approach for physical security would not provide the flexibility needed to deal with the widely varying risk profiles and circumstances across the North American grid and would instead create unnecessary and inefficient regulatory burdens and compliance obligations.” Letter available at: https://securethegrid.com/wp-content/uploads/2021/05/NERC-Response-to-Senators-Letter-Reid-2-11-14-v4.pdf
[17] See: https://securethegrid.com/oe-417-database/
[18] See for example: Smith, Rebecca. Wall Street Journal. “How America Could Go Dark.” July 14, 2016. https://www.wsj.com/articles/how-america-could-go-dark-1468423254
[19] See Exhibit A.
[20] See 171 FERC ¶ 61,205. https://elibrary.ferc.gov/eLibrary/idmws/file_list.asp?document_id=14867700
[21] See FERC Order No. 779, issued May 16, 2013 at 143 FERC ¶ 61,147 https://elibrary.ferc.gov/eLibrary/filelist?document_id=14115712&optimized=false
[22] See FERC Docket RM15-11-000. Multiple experts outside the electric industry argue that the standard is not sufficient to protect the grid from a GMD event.
[23] See Exhibit B.
[24] See 173 FERC ¶ 61,010. https://elibrary.ferc.gov/eLibrary/filelist?accession_num=20201002-3033
[25] See FERC Docket AD17-9-000 Petition for Rulemaking by the Foundation for Resilient Societies in a New Docket: For the Commission to Require an Enhanced Reliability Standard to Detect, Report, Mitigate and Remove Malware from the Bulk Power System.
[26] See February 14, 2019 Senate Committee on Energy and Natural Resources hearing: “Hearing to Consider the Status and Outlook for Cybersecurity Efforts in the Energy Industry” (at 1 hour and 30 minutes). Available at: https://securethegrid.com/senate-cybersecurity-hearing/
[27] See: https://dshs.texas.gov/news/updates.shtm#wn
[28] See: https://www.dallasfed.org/research/economics/2021/0415.aspx
[29] Attached as Exhibit C is the complaint on the inadequacy of the reliability standards and their failure to prevent the Texas grid collapse of February 2021 filed with FERC on February 28, 2021.
[30] See 175 FERC ¶ 61,163. https://elibrary.ferc.gov/eLibrary/filelist?accession_num=20210526-3061
[31] Commission to Assess the Threat to the United States from Electromagnetic Pulse (EMP) Attack. Reports are available here: https://securethegrid.com/unclassified-emp-commission-reports/
[32] See: https://securethegrid.com/epri-emp-report/
[33] Electromagnetic Defense Task Force (EDTF) Review of EPRI EMP Report August 23, 2109. http://bit.ly/2OglqYI
[34] Department of Energy. “Physical Characteristics of HEMP Waveform Benchmarks for Use in Assessing Susceptibilities of the Power Grid, Electrical Infrastructures, and Other Critical Infrastructure to HEMP Insults.” January 11, 2021. https://bit.ly/3rLmztL
[35] See: https://securethegrid.com/electric-industry-lobbyists-china-ties-questioned/
[36] See: “Implications of Power Blackouts For The Nation’s Cybersecurity and Critical Infrastructure Protection,” Before the US House, Joint Hearing of the Subcommittee on Cybersecurity, Science, and Research and Development, and the Subcommittee on Infrastructure and Border Security of the Select Committee On Homeland Security, (108th Congress) September 4 & 23, 2003. http://bit.ly/2qV9La3
[37] General Accounting Office (GAO). Federal Electrical Emergency Preparedness Is Inadequate. EMD-81-50. May 12, 1981. http://bit.ly/354ZN4i
[38] See: Defense Civil Preparedness Agency (DCPA). Vulnerability of Regional and Local Electric Power Systems– Nuclear Weapons Effects and Civil Defense Actions. July 1975. http://bit.ly/2QogiVj
[39] Testimony of Mark N. Cooper, Director of Research, Consumer Federation of America. Page 25. “Keeping The Lights On: The Federal Role In Managing The Nation’s Electricity.” Before the Committee on Governmental Affairs, Oversight of Government Management, the Federal Workforce and the District of Columbia Subcommittee. (108th Congress) September 10, 2003. http://bit.ly/357GCHh
[40] ProPublica. “Four Types of Scandals Utility Companies Get Into With Money From Your Electric Bills.” October 10, 2020. https://www.propublica.org/article/four-types-of-scandals-utility-companies-get-into-with-money-from-your-electric-bills
[41] Hartman, Devin and Haugh, Mike. R Street Institute. “Electric Competition: The Antidote For Bad Behavior.” September 2020. https://www.rstreet.org/wp-content/uploads/2020/09/Final-No-205-electric-competition-updated.pdf
[42] Available at: https://securethegrid.com/oe-417-database/
[43] Available at https://www.nerc.com/pa/RAPA/PA/Pages/default.aspx
[44] Note that the report each year is on the previous year, e.g., the 2020 report is for the events of the year 2019.
[45] See, for example: E&E News. “’Cyber event’ disrupted U.S. grid networks — DOE” April 30, 2019. https://www.eenews.net/stories/1060242741/ and E&E News. “Report reveals play-by-play of first U.S. grid cyberattack.” September 6, 2019. https://www.eenews.net/stories/1061111289. Ironically, NERC posted a “Lessons Learned” document on this cyberattack to the industry, but still told the public “There were no reportable cyber or physical security incidents in 2019.”
[46] Holstege, Sean and Randazzo, Ryan, The Republic. “Sabotage at Nogales station puts focus on threats to grid.” June 13, 2014. https://www.azcentral.com/story/news/arizona/2014/06/12/sabotage-nogales-station-puts-focus-threats-grid/10408053/
[47] Smith, Rebecca. The Wall Street Journal. “Assault on California Power Station Raises Alarm on Potential for Terrorism.” February 5, 2014. https://www.wsj.com/articles/assault-on-california-power-station-raises-alarm-on-potential-for-terrorism-1391570879
[48] Government Accountability Office. CRITICAL INFRASTRUCTURE PROTECTION: Cybersecurity of the Nation’s Electricity Grid Requires Continued Attention. October 21, 2015. http://bit.ly/39kNp3p
[49] National Cybersecurity and Communications Integration Center. “FY 2016 Incidents by Sector.” https://www.us-cert.gov/sites/default/files/Annual_Reports/Year_in_Review_FY2016_IR_Pie_Chart_S508C.pdf
[50] Idaho National Laboratory. “Cyber Threat and Vulnerability Analysis of the U.S. Electric Sector.” August 2016. https://www.energy.gov/sites/prod/files/2017/01/f34/Cyber%20Threat%20and%20Vulnerability%20Analysis%20of%20the%20U.S.%20Electric%20Sector.pdf
[51] Details of the FOIA requests and responses as well as the lawsuit are available here: https://securethegrid.com/cip-violation-database/
[52] Available at: https://www.wsj.com/articles/SB123914805204099085
[53] Available at: https://www.wsj.com/articles/americas-electric-grid-has-a-vulnerable-back-doorand-russia-walked-through-it-11547137112
[54] Available at: https://www.wsj.com/articles/suspected-russian-hack-extends-far-beyond-solarwinds-software-investigators-say-11611921601
[55] Available at: https://elibrary.ferc.gov/idmws/file_list.asp?document_id=14756159
[56] 16 U.S. Code § 824o(b)(1) (Electric reliability) provides that: “The Commission shall have jurisdiction, within the United States, over the ERO certified by the Commission under subsection (c), any regional entities, and all users, owners and operators of the bulk-power system, including but not limited to the entities described in section 824(f) of this title, for purposes of approving reliability standards established under this section and enforcing compliance with this section. All users, owners and operators of the bulk-power system shall comply with reliability standards that take effect under this section.” [Emphasis added.]
[57] For further details, see Motion to Intervene in FERC Docket NP19-4-000 available at: https://securethegrid.com/wp-content/uploads/2019/02/FERC-Docket-NP19-4-Motion-to-Intervene-Mabee.pdf; Reply Comments in FERC Docket NP19-4-000 available at: https://securethegrid.com/wp-content/uploads/2019/05/Reply-Comments-of-Michael-Mabee-in-NP19-4-000.pdf; Petition for Rulemaking available at: https://securethegrid.com/wp-content/uploads/2019/02/Petition-for-Rulemaking-Mabee-with-exhibits-1.pdf
[58] See report: https://securethegrid.com/pge-endangered-the-grid/
[59] Robert McMillan, Joseph De Avila and Jacob Bunge. Wall Street Journal. “NYC’s Subway Operator and Martha’s Vineyard Ferry Latest to Report Cyberattacks. Attacks on infrastructure are part of a global criminal pivot from stealing data to hobbling operations” June 2, 2021. https://www.wsj.com/articles/ransomware-scourge-continues-as-essential-services-are-hit-11622672685
[60] See: https://www.cisa.gov/critical-infrastructure-sectors
[61] After the Enron debacle, Congress enacted similar certification requirements for publicly traded companies related to financial and disclosure controls. See sections 302, 404 and 906 of the Sarbanes-Oxley Act of 2002 and it’s implementing regulations at 17 CFR §§228-240.
[62] Exhibit F is an example of such a provision contemplated by Senators Grassley and Markey in 2020.
[wpedon id=”5868″ align=”center”]