PG&E endangered the grid – and tried to cover it up
PG&E Endangered The Grid – And Endangered You
 Today the Wall Street Journal’s Rebecca Smith reported:
Today the Wall Street Journal’s Rebecca Smith reported:
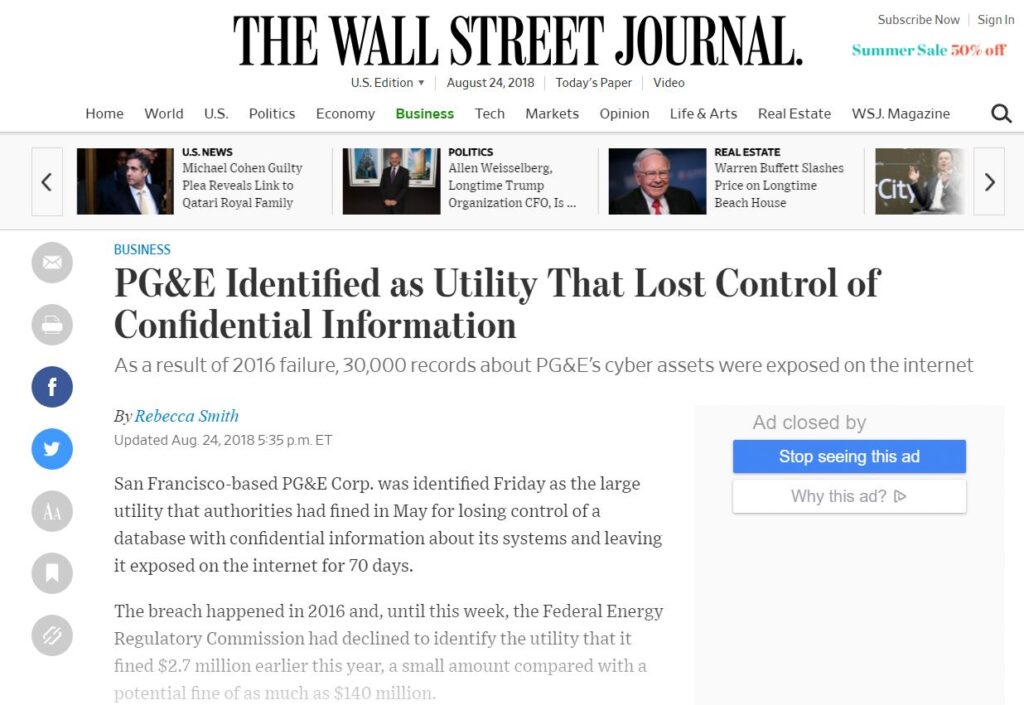
“PG&E Identified as Utility That Lost Control of Confidential Information. As a result of 2016 failure, 30,000 records about PG&E’s cyber assets were exposed on the internet.”
We have been talking about the NERC cover-up (and FERC cover up) for quite some time. Now we finally know that PG&E endangered the grid and attempted to cover it up – with the help of NERC and FERC.
The PG&E Cyber Breach.
On May 30, 2016 cyber security researcher Chris Vickery reported on a massive cyber-breach he had discovered involving Pacific Gas and Electric (PG&E). (See: “Pacific Gas and Electric Database Exposed.”) According to Mr. Vickery:
“Among other things, it contained details for over 47,000 PG&E computers, virtual machines, servers, and other devices. All of it completely unprotected. No username or password required for viewing. We’re talking about IP addresses, operating systems, hostnames, locations, MAC addresses, and more. This would be a treasure trove for any hostile nation-state hacking group. That’s not to mention the 120 hashed employee passwords, or the plaintext NTLM, SOAP, and mail passwords.”
PG&E denied that there was a breach, initially stating that the data was fake. This claim was later refuted. Essentially, PG&E lied to try to cover this up.
The “Unidentified Registered Entity” Cyber Breach.
 Fast forward to February 28, 2018. NERC filed a regulatory document with FERC entitled: “NERC Full Notice of Penalty regarding Unidentified Registered Entity.” In this filing, NERC, without identifying the culprit, regales FERC with a tale of an epic cyber breach. The details provided by NERC are vague (likely in order to protect the guilty). At an unknown date in the past – but likely 2016 based on the “NERC Violation ID” number on page 2 – the NERC-anonymized entity experienced a horrific data breach. According to NERC, this data breech involved “30,000 asset records, including records associated with Critical Cyber Assets (CCAs). The records included information such as IP addresses and server host names.”
Fast forward to February 28, 2018. NERC filed a regulatory document with FERC entitled: “NERC Full Notice of Penalty regarding Unidentified Registered Entity.” In this filing, NERC, without identifying the culprit, regales FERC with a tale of an epic cyber breach. The details provided by NERC are vague (likely in order to protect the guilty). At an unknown date in the past – but likely 2016 based on the “NERC Violation ID” number on page 2 – the NERC-anonymized entity experienced a horrific data breach. According to NERC, this data breech involved “30,000 asset records, including records associated with Critical Cyber Assets (CCAs). The records included information such as IP addresses and server host names.”
According to NERC’s filing:
“These violations posed a serious or substantial risk to the reliability of the bulk power system (BPS). The CCAs [Critical Cyber Assets] associated with the data exposure include servers that store user data, systems that control access within URE’s Control centers and substations, and a supervisory control and data acquisition (SCADA) system that stores critical CCA Information. The data was exposed publicly on the Internet for 70 days. The usernames of the database were also exposed, which included cryptographic information of those usernames and passwords.
Exposure of the username and cryptographic information could aid a malicious attacker in using this information to decode the passwords. This exposed information increases the risk of a malicious attacker gaining both physical and remote access to URE’s systems. A malicious attacker could use this information to breach the secure infrastructure and access the internal CCAs by jumping from host to host within the network. Once in the network, the attacker could attempt to login to CCAs, aided by the possession of username and password information.”
Disturbingly, The data associated with the Critical Cyber Assets was accessible on the internet for a total of 70 days and, according to the NERC filing, “WECC cannot confirm that another third party did not capture and retain possession of the exposed data.” (I’m sure Russia, China, Iran and North Korea have no intention of misusing this data if they have it.)
Apparently, the culprit agreed to “settle” the issue with the Western Electricity Coordinating Council (WECC). In the mind-numbingly complex self-regulatory scheme of the electric grid, WECC is one of the regional entities that reports to NERC. NERC is a non-profit organization that purportedly functions as the “Electric Reliability Organization.” Ultimately, penalties and actions of this type (in this case a settlement agreement) must be approved by FERC. We have not seen the settlement agreement. That is one of the problems here. All we have is a brief summary:
“According to the Settlement Agreement, URE neither admits nor denies the violations, but has agreed to the assessed penalty of two million seven hundred thousand dollars ($2,700,000), in addition to other remedies and actions to mitigate the instant violations and facilitate future compliance under the terms and conditions of the Settlement Agreement.”
In this case, somebody – whether it be the customers or the shareholders – is going to pay the $2.7 million dollars. Don’t they have a right to know they are paying for this? In fact, if the “Unidentified Registered Entity” is a publicly traded company, would they not be required to disclose to the investors and public the fact they they were involved in this potentially catastrophic cyber breach? The SEC rules would seem to indicate that this is the case. Click for 2/26/2018 guidance. Click here for October 13, 2011 guidance.
The Truth Comes Out: PG&E Endangered the Grid
Well, today we finally have confirmation that the “Unidentified Registered Entity” is PG&E Corp. So, PG&E endangered the grid and then tried to cover it up. PG&E Corp is a publicly traded company. (NYSE: PCG.) Sorry shareholders – you lose.
 The Secure The Grid Coalition has been fighting this battle to get the government to disclose the miscreant and was even quoted in the article:
The Secure The Grid Coalition has been fighting this battle to get the government to disclose the miscreant and was even quoted in the article:
“PG&E’s identity was revealed because of a Freedom of Information Act request filed to FERC by Secure the Grid Coalition, a nonprofit group focused on critical infrastructure protection. Michael Mabee, a New Hampshire representative of the group, said he petitioned for the information, because he thought it was “disturbing and wrong” for federal officials to protect a utility whose actions endangered the public.”
Thank you, Rebecca Smith and the Wall Street Journal for helping us to hold the utilities and the government accountable for the safety of the critical infrastructure.
Case Closed!
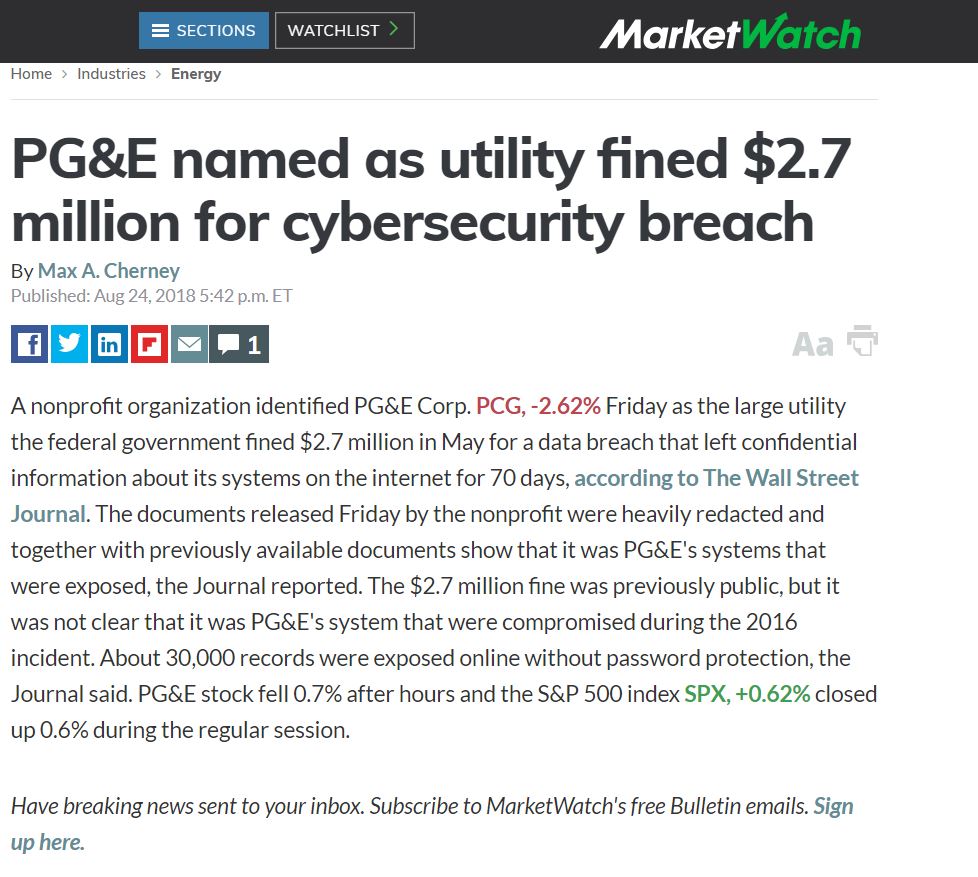
Note: MarketWatch has also picked up on the story:
[wpedon id=”5868″ align=”center”]