Now It’s a FERC Cover-Up
The NERC Cover-Up Just Became a FERC Cover-Up
The Federal Energy Regulatory Commission (FERC) just did an astonishing thing: They adopted the North American Electric Reliability Corporation (NERC) cover-up, making it officially a FERC cover-up. The issue? A large utility company endangered our lives with a massive cyber breach and the industry – and now the government – does not want us to know “who done it.”
 Perhaps some background to this gut-punch is in order. This incident is of critical importance to you and your family but the FERC cover-up is hidden behind a web of bureaucratic fog. This incident is disturbing because the primary federal regulator for the electric grid – the critical infrastructure on which we all depend – is a government agency (FERC) that has now proven itself to be a patsy for the electric utility industry.
Perhaps some background to this gut-punch is in order. This incident is of critical importance to you and your family but the FERC cover-up is hidden behind a web of bureaucratic fog. This incident is disturbing because the primary federal regulator for the electric grid – the critical infrastructure on which we all depend – is a government agency (FERC) that has now proven itself to be a patsy for the electric utility industry.
The grid is “self regulated.” This means that we depend on the thousands of companies that comprise the grid to do the right thing. It is basically an honor system. If one of these thousands of companies does not do the right thing (e.g., endangers us by having dorked-up cyber security), it is not the government that acts – it is the industry itself, through the industry mouthpiece, the North American Electric Reliability Corporation (NERC). For more information on how the grid is regulated, click here.
In this case – an egregious violation of national security – the industry response amounts to an “oopsy.” And now the federal government has bought off on this. Let’s look at the whole FERC cover-up in more detail.
Timeline of a FERC Cover-Up:
The PG&E Cyber Breach.
On May 30, 2016 cyber security researcher Chris Vickery reported on a massive cyber-breach he had discovered involving Pacific Gas and Electric (PG&E). (See: “Pacific Gas and Electric Database Exposed.”) According to Mr. Vickery:
“Among other things, it contained details for over 47,000 PG&E computers, virtual machines, servers, and other devices. All of it completely unprotected. No username or password required for viewing. We’re talking about IP addresses, operating systems, hostnames, locations, MAC addresses, and more. This would be a treasure trove for any hostile nation-state hacking group. That’s not to mention the 120 hashed employee passwords, or the plaintext NTLM, SOAP, and mail passwords.”
Here are a few articles from the time of the incident:
- “One of California’s largest utilities reportedly left a hacker ‘treasure trove’ wide open.” Paul Szoldra, Business Insider. March 31, 2016.
- “Database of California Electric Utility Exposed Online.” Eduard Kovacs, SecurityWeek. May 31, 2016.
- “US electricity provider accused of malpractice for leaving 47,000 computers exposed to hacking.” Jason Murdock, International Business Times. May 31, 2016.
PG&E denied that there was a breach, initially stating that the data was fake. This claim was later refuted. Essentially, PG&E lied to try to cover this up.
- “Pacific Gas and Electric Claims Recent Data Breach Only Exposed Fake Details. PG&E denies any wrongdoing, says it was only a test server.” Catalin Cimpanu, Softpedia News. May 31, 2016.
- “Pacific Gas & Electric Claims Data Leak Was Fake.” ZeroSecurity News. May 31, 2016.
This was no minor incident to cyber security and IT professionals and the misleading information PG&E provided was remarkable. A year later, they were still talking about it:
- “15 famous ERP disasters, dustups and disappointments. 5. PG&E: When ‘sample’ data isn’t.” Josh Fruhlinger, ARN/IDG. July 11, 2017.
One would hope that with something this flagrant – a horrible cyber breach along with PG&E lying about it – some regulator would step in. Unfortunately.we have to depend on the industry to police itself. The results, we find are far from acceptable. What is even more disappointing is that this ends up becoming a FERC cover-up when FERC had every opportunity to do the right thing.
The “Unidentified Registered Entity” Cyber Breach.
Fast forward to February 28, 2018. NERC filed a regulatory document with FERC entitled: “NERC Full Notice of Penalty regarding Unidentified Registered Entity.” In this filing, NERC, without identifying the culprit, regales FERC with a tale of an epic cyber breach. The details provided by NERC are vague (likely in order to protect the guilty). At an unknown date in the past – but likely 2016 based on the “NERC Violation ID” number on page 2 – the NERC-anonymized entity experienced a horrific data breach. According to NERC, this data breech involved “30,000 asset records, including records associated with Critical Cyber Assets (CCAs). The records included information such as IP addresses and server host names.”
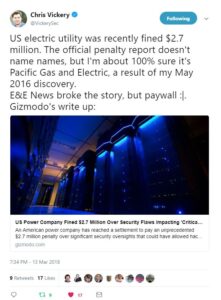
This sounds amazingly similar to the PG&E cyber breach exposed by Mr. Vickery in 2016. In fact, Mr. Vickery even thinks this “Unidentified Registered Entity” is PG&E.
According to NERC’s filing:
“These violations posed a serious or substantial risk to the reliability of the bulk power system (BPS). The CCAs [Critical Cyber Assets] associated with the data exposure include servers that store user data, systems that control access within URE’s Control centers and substations, and a supervisory control and data acquisition (SCADA) system that stores critical CCA Information. The data was exposed publicly on the Internet for 70 days. The usernames of the database were also exposed, which included cryptographic information of those usernames and passwords.
Exposure of the username and cryptographic information could aid a malicious attacker in using this information to decode the passwords. This exposed information increases the risk of a malicious attacker gaining both physical and remote access to URE’s systems. A malicious attacker could use this information to breach the secure infrastructure and access the internal CCAs by jumping from host to host within the network. Once in the network, the attacker could attempt to login to CCAs, aided by the possession of username and password information.”
Disturbingly, The data associated with the Critical Cyber Assets was accessible on the internet for a total of 70 days and, according to the NERC filing, “WECC cannot confirm that another third party did not capture and retain possession of the exposed data.” (I’m sure Russia, China, Iran and North Korea have no intention of misusing this data if they have it.)
Apparently, the culprit agreed to “settle” the issue with the Western Electricity Coordinating Council (WECC). In the mind-numbingly complex self-regulatory scheme of the electric grid, WECC is one of the regional entities that reports to NERC. NERC is a non-profit organization that purportedly functions as the “Electric Reliability Organization.” Ultimately, penalties and actions of this type (in this case a settlement agreement) must be approved by FERC. We have not seen the settlement agreement. That is one of the problems here. All we have is a brief summary:
“According to the Settlement Agreement, URE neither admits nor denies the violations, but has agreed to the assessed penalty of two million seven hundred thousand dollars ($2,700,000), in addition to other remedies and actions to mitigate the instant violations and facilitate future compliance under the terms and conditions of the Settlement Agreement.”
 In my mind, there are three major public policy issues here and members of the Secure The Grid Coalition brought these issues to the attention of FERC:
In my mind, there are three major public policy issues here and members of the Secure The Grid Coalition brought these issues to the attention of FERC:
- There is a prompt reporting requirement. It is unclear whether whether the Electric Reliability Organization (NERC) or the Regional Entity (WECC) “report[ed] promptly to the Commission any self-reported violation or investigation of a violation or an alleged violation of a Reliability Standard” in accordance with 18 CFR § 39.7(b).
- Identity of the “Unidentified Registered Entity.” NERC’s lack of transparency by hiding the identity of the “Unidentified Registered Entity” from the public is against the public interest and should not be allowed by the Commission.
- The terms of the settlement agreement are suspicious and should be reviewed by the commission to insure that they are fair and in the public interest. The relatively light penalty and non-admission clause raise immediate concerns. If the Western Electricity Coordinating Council truly concluded, as NERC states, that two violations of the Critical Infrastructure Protection (CIP) Reliability Standards were committed, why is the entity being allowed to enter an agreement where it “neither admits nor denies the violations”? Such an agreement is against the public interest as it does not serve as a deterrent for future violations in the industry. What strong incentive is there for regulated entities to adhere to Critical Infrastructure Protection (CIP) Reliability Standards if the penalties are light, they do not have to admit fault for violations, and their identity will not be disclosed.
With something this bad, in what possible world is it okay that the terms of the settlement agreement and the name of the “Unidentified Registered Entity” is kept from the public and the company’s shareholders? In any regulatory scheme that I have ever seen, this odious practice would not be allowed. Take for example the self regulatory scheme on Wall Street. Disclosure is the cornerstone of the self regulatory structure of the financial industry – and disclosure is rigorously enforced by the U.S. Securities and Exchange Commission.
In this case, somebody – whether it be the customers or the shareholders – is going to pay the $2.7 million dollars. Don’t they have a right to know they are paying for this? In fact, if the “Unidentified Registered Entity” is a publicly traded company, would they not be required to disclose to the investors and public the fact they they were involved in this potentially catastrophic cyber breach? The SEC rules would seem to indicate that this is the case. Click for 2/26/2018 guidance. Click here for October 13, 2011 guidance.
Pants (still) on fire.
Finally, there is the small matter that after lying to the press about the incident, the evasiveness and lying continued. According to the NERC filing, “URE [Unidentified Registered Entity] was not fully transparent and forthcoming with all pertinent information detailing the data exposed in the incident. Specifically, URE did not provide WECC initially with all the data fields exposed in the incident.”
Uhhh, isn’t “not fully transparent and forthcoming” just a fancy way of saying they were still lying? So, surely, FERC would not allow such a cover-up to exist on their watch, right?
Here are a few of the news articles that came out after the NERC filing on February 28, 2018.
- “Grid regulator issues ‘massive’ penalty over data exposure.” Blake Sobczak, E&E News. March 5, 2018.
- “NERC fines utility $2.7 million for cyber breach.” Energy Policy Update. March 9, 2018.
- “Data Exposure by Vendor Leads to $2.7 Million NERC Penalty for Utility.” Morgan Lewis. March 9, 2018.
- “US Power Company Fined $2.7 Million Over Security Flaws Impacting ‘Critical Assets’.” Dell Cameron, Gizmodo. March 13, 2018.
- “U.S. Energy Firm Fined $2.7 Million Over Data Security Incident.” Eduard Kovacs, SecurityWeek. March 14, 2018.
- “Grid Cybersecurity: The Critical Infrastructures Are Under Attack.” Michael Mabee. March 25, 2018.
- “A NERC Cover-Up? Who Put the Electric Grid at Risk?” Michael Mabee. April 1, 2018.
- “The Electric Utility Industry Lacks Effective Regulation.” Michael Mabee. April 16, 2018.
- “FERC pressed to name names in cybersecurity fine.” Blake Sobczak, E&E News. April 17, 2018.
The FERC Cover-Up.
In the docket, there were four submissions from experts (three from members of the STG Coalition) requesting the FERC review the incident and settlement:
- Motion to Intervene of Michael Mabee [Click here for .PDF file]
- Motion to Intervene of of Public Citizen, Inc. and The Utility Reform Network [Click here for .PDF file]
- Comments of Comments of Foundation for Resilient Societies and Isologic LLC [Click here for .PDF file]
- Comments of Frank J. Gaffney, Jr., President & CEO, Center for Security Policy [Click here for .PDF file]
All had essentially the same Quixotic request: that FERC review the incident and release the name of the “Unidentified Registered Entity.” Alas, we were apparently tilting at windmills. A mere 4 business hours after the docket closed, FERC gave the electric utility industry a pass on this total lack of accountability. The NERC cover-up became a FERC cover-up.
- “FERC approves $2.7M cyber fine without naming names.” Blake Sobczak, E&E News. May 31, 2018.
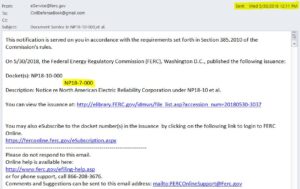
FERC aided and abetted this cover-up shamelessly and quickly, giving no consideration to four expert comments in the docket: The docket closed at 5:00 p.m. on May 30, 2018. The following day at 12:11 p.m. (just after noon), FERC dismissed the docket with an order adopting the NERC cover-up. Couldn’t they have at least waited a few days to give the false appearance that they were considering the public comments and two motions to intervene?? That would have at least made us feel better.
The email I received above linked to a FERC Order in which the penalties NERC proposed against the “Unidentified Registered Entity” involved in a massive cyber breach are now “deemed affirmed by operation of law.”
To make matters worse, as you may know, I had submitted a Freedom of Information Act Request seeking the name of the “Unidentified Registered Entity.” [Click here to see my FOIA request.] FERC Denied my FOIA request on May 25, 2018.[Click here to see FERC’s denial letter.] So this is not an accident. FERC is actively seeking to cover up the identity “Unidentified Registered Entity” for their chums in the electric utility industry. This is now a federal government FERC cover-up.
Well played NERC – you are now the proud owner of a government agency.
